Getting In The Fight
Let’s talk about how to be effective detecting intruders. Or what we at Sandfly Security simply call:
Getting in the fight.
First to lay some groundwork, the policy of Sandfly Security is that we don’t release attack tools and do not discuss exploit tactics except in high-level terms to demonstrate how to detect and mitigate attacks. Doing otherwise violates the trust we built with our customers and the community.
However, the one thing we do believe in is this: Getting in the fight. Getting in the fight means discussing tactics used by intruders and releasing tools to help secure your systems against attack. The end goal is to get adversaries to change and re-tool their tactics because they no longer work. Re-tooling is expensive and, as they say, imposes cost on your adversaries.
Are You Effective?
As anyone in the security space will tell you, it’s very hard to get adequate budget for security often because it’s difficult to prove your value. Good security means attackers are detected and stopped. If you stop them, then they can’t do harm. However if you stop them that also means you can’t show what would have happened if they had achieved their goals. Security teams and products are in the unenviable position of trying to prove a negative.
Can you prove Santa Claus does not exist?
Can you prove that if we don’t deploy good security it would cost us more in lost revenue?
Security staff are faced with the dilemma of trying to prove they are valuable but without a direct measurable profit. Security is often different than a company’s main business. You sell a widget and you get X dollars. Finance teams understand that equation and it works in a spreadsheet. But how do you show value when they can’t attach a dollar figure because you stopped something from happening? How do you prove you’re effective?
Don’t Be Ignored
One way to prove effectiveness is to cause your adversaries to change their tactics to work around your defenses. If you can show you forced them to change their tactics, then you are being effective. If you stopped them enough that they moved onto an easier target, then you are being effective. You are in the fight and can show your value even though you can’t attach a dollar figure to it directly.
Even more than being in the fight, you are not being ignored. Using a security tool or tactic that is ignored means it is not effective. Attackers that ignore your security defenses do not think they are a particular risk and are not going to waste any time working to counter them. This is not where you want to be when designing your defense strategy.
As security practitioners, we want attackers to know we’re here and they can’t ignore us. We want them to deploy countermeasures and other tactics to deal with us. This means what we are doing is causing adversaries pain and this is the entire point of what we do. Not being ignored is the primary goal of anyone in information security. Get in the fight so you can be effective and can’t be ignored.
Fighting With Entropy
As an example of getting in the fight, we released a simple open source tool called sandfly-filescan (now renamed to sandfly-entropyscan). This tool scans your system and will tell you if it finds a Linux executable file that has high entropy. High entropy means the file is very random and likely packed or encrypted which is common with malware to avoid detection. Packed or encrypted binaries make reverse engineering harder as well. Both of these things are great for malware, but bad for defenders. Unsurprisingly, a good amount of Linux malware is packed or encrypted because it is an effective tactic for intruders.
However, if you know most all binaries on Linux are not packed or encrypted, then looking for high entropy files becomes a great way to find malware. Simple and effective. We like doing simple things that are effective. When you use many simple detection methods it builds an advanced detection net without impacting system operations. As it were, since at least 99% of all binaries on Linux are never going to be packed or encrypted, when you run across one it immediately should draw your attention.
Sandfly-filescan eliminates the entire class of packed or encrypted binary evasion for malware authors. In the past using a packed or encrypted binary was effective for hiding. However with the free tool we released using packing or encryption to hide actually makes malicious binaries extremely easy to spot. Packing or encryption as an evasion tactic is now a liability for malware authors and they need to do something else. Congratulations, you are in the fight!
Forcing A Response
After releasing this tool we figured it would make some malware authors unhappy because they’d have to change their tactics. It turns out we didn’t have to wait long to see a response. About three weeks after we released the tool in December 2019 an aggressive piece of Linux malware began spreading and tried to bypass sandfly-filescan. When we looked at the malware script we saw some interesting things.
First, we love Star Trek and were happy to see some nice ASCII art tribute to the Enterprise at the top.

Next, a tip of the hat to fellow fighter Troy Mursch at Bad Packets for making the cut. Bad Packets traces malicious network activity and has a very active Twitter account worth following.
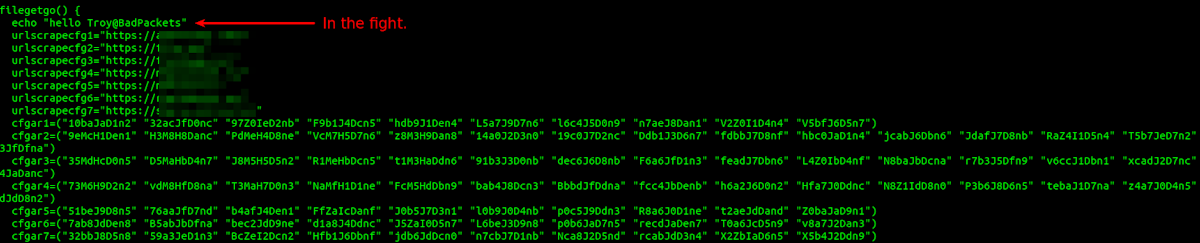
Finally, we see sandfly-filescan and reference (Craig Rowland founder of Sandfly) in the Honor Roll. This is an attempt by the script to find the utility and try to stop it if running. It also tries to delete it and set the filename immutable so it can’t be replaced.

Of course, the malware used a packed executable to run so it was easily found by our free tool (and our commercial product). At the time almost no Virus Total engines were reporting they could see it, yet the high entropy was plainly obvious to Sandfly that this binary was malicious. The fact that it was packed with high entropy was a primary indicator it was up to no good. Everything else it did were just the details.
Get In The Fight
The above is just an example of how getting in the fight, even with what you think is something simple, can be highly effective. Here we obtained validation that the detection tactic of entropy scanning is effective because we forced an adversary to respond. This is why we do it in our full product on a larger scale.
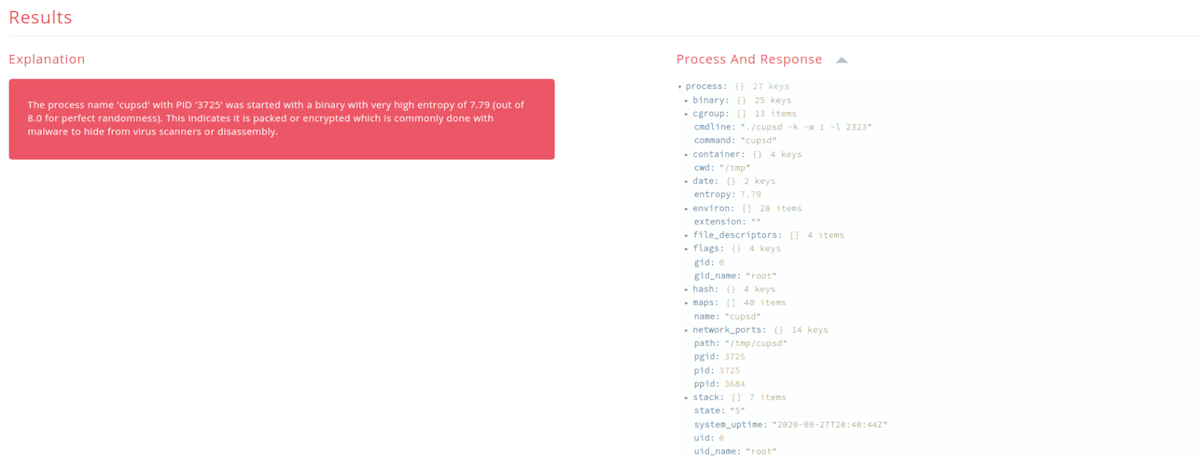
High entropy executable files:
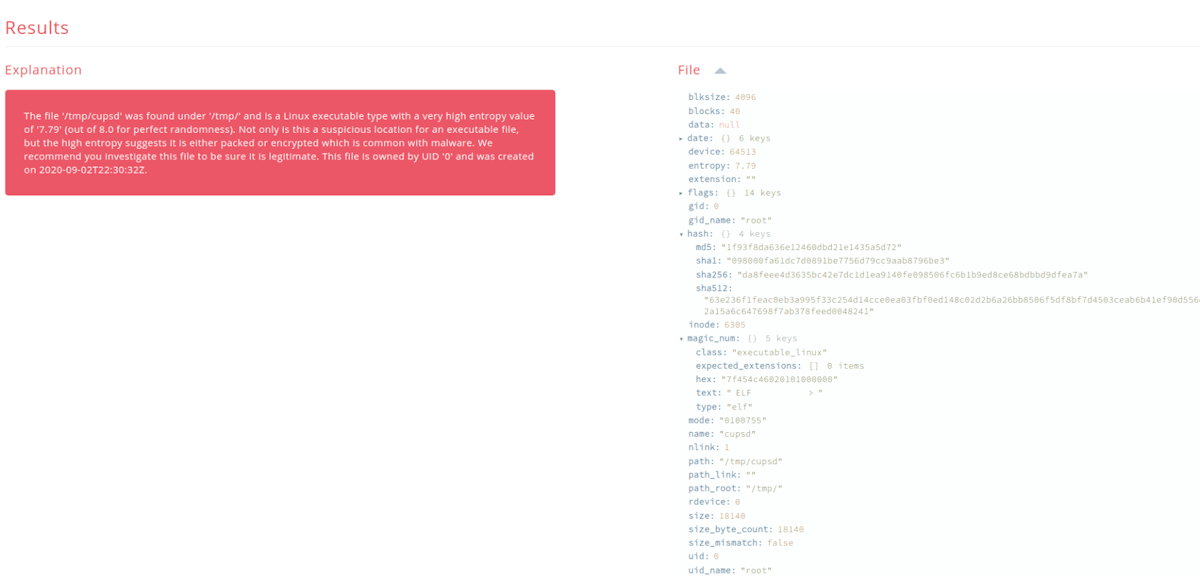
Be Effective
Disrupting adversary tactics is just one way to get in the fight. When thinking of your security defenses, consider how adversaries respond. If what you’re doing is being ignored, you aren’t being effective. Get in the fight!