Security Monitoring for Threats on Embedded Linux
A new report from Mandiant entitled: Eye Spy on Your Email details a series of sophisticated attacks against embedded network devices often running Linux. In particular, the report states (emphasis added):
Part of the group’s success at achieving such a long dwell time can be credited to their choice to install backdoors on appliances within victim environments that do not support security tools, such as anti-virus or endpoint protection. The high level of operational security, low malware footprint, adept evasive skills, and a large Internet of Things (IoT) device botnet set this group apart and emphasize the “advanced” in Advanced Persistent Threat.
This report was interesting because it acknowledges that lack of visibility into Linux appliances is being actively leveraged for advanced threat purposes. We agree. Lack of visibility into embedded Linux devices is a huge problem and is why Sandfly works on them without needing to deploy any agents.
Linux Embedded Device Risk is Underrated
Embedded Linux devices are underrated as an attack vector. Yet, the reality is an embedded Linux device like a $30 Raspberry Pi is incredibly capable with 4-8GB of RAM and a decent CPU. Loaded with Linux, it is a great environment to move in attack tools and initiate lateral movement inside a network. Similar capabilities exist across other embedded Linux devices. Even a simple Linux based webcam is surprisingly capable if put in the hands of an attacker.
However, embedded devices are often ignored and left to fend for themselves with no patches applied and little attention as to what is actually going on inside them. As NASA found out not long ago, this is a great way to get compromised and allow someone to remain hidden for a very long time.
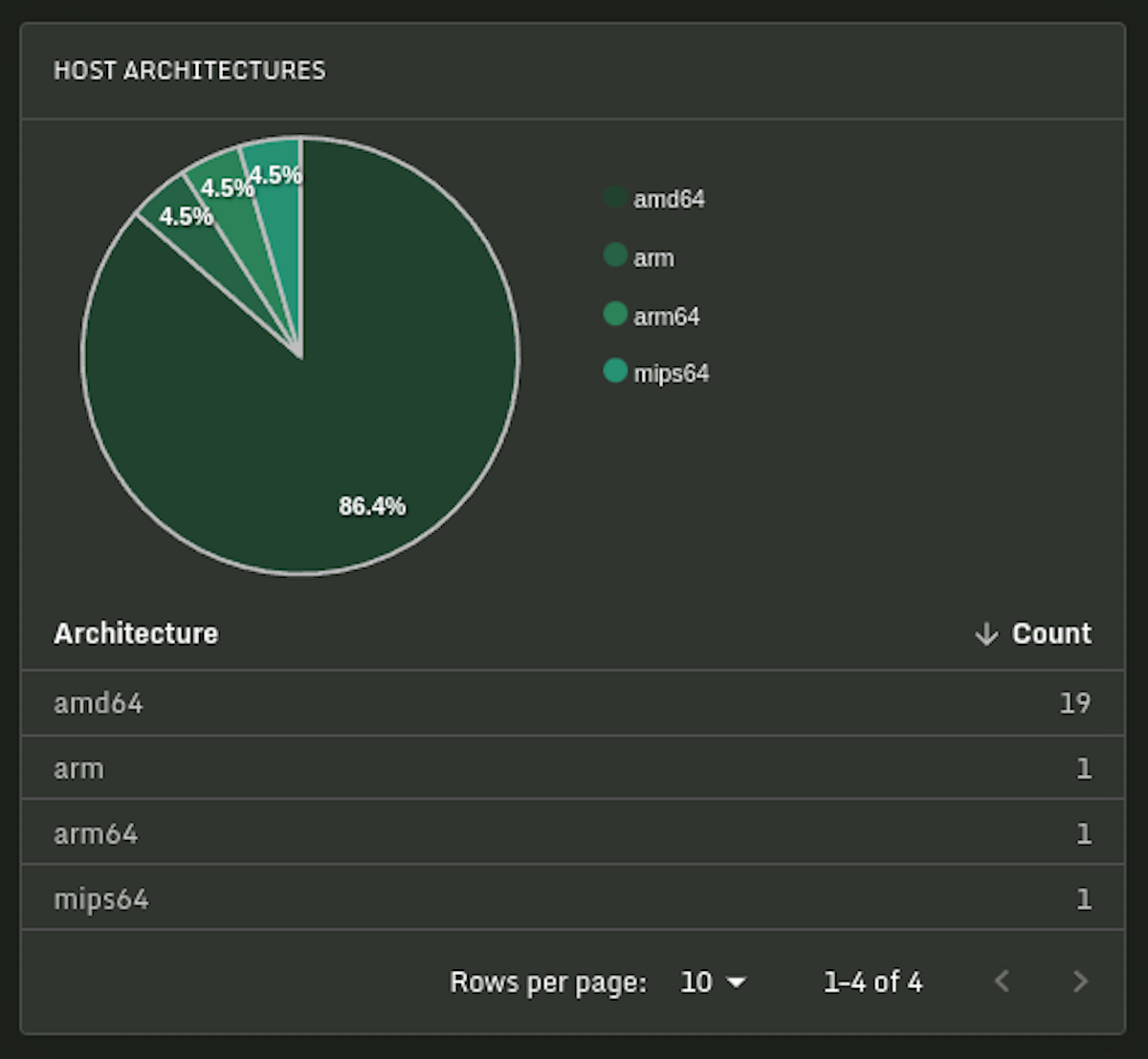
At Sandfly we have a particular interest in this area as we specialize in agentless security for Linux. In particular, we in fact can run on embedded Linux devices that support SSH access and work instantly across systems running Intel, AMD, Arm and MIPS CPUs.
Embedded Devices Often Are Critical
If an embedded Linux device gets compromised, the attacker has a very powerful system at their disposal to press an attack. Even worse, the devices are often part of the critical network infrastructure such as an access point, firewall or VPN. This means attackers on these devices can directly intercept and manipulate traffic that passes through. For instance, a compromised VPN router means an attacker can easily siphon off unencrypted traffic, steal keys, insert VPN access credentials and much more. The VPNFilter malware did exactly this.
Combine the above with almost total lack of monitoring and no patches, and it's no surprise that Linux devices are being targeted for attack by people that know what they're doing.
Why Agentless for Embedded Linux
The lack of monitoring on embedded Linux is because agent-based solutions often cannot run on these devices for a variety of reasons such as:
Limited CPU.
Limited RAM.
Limited drive space.
Risk of bricking the device with kernel monitoring.
Non-standard CPU such as Arm or MIPS.
Old Linux versions that are not supported.
No ability to update devices with latest agents without disruption.
Etc.
Sandfly however is agentless and has no problems running in this capacity and in fact is used today by customers in exactly this application. Sandfly has extremely wide compatibility with none of the traditional risks of agent-based EDR monitoring.
Below we see Sandfly monitoring a variety of Linux distributions, kernel versions, CPUs and more.
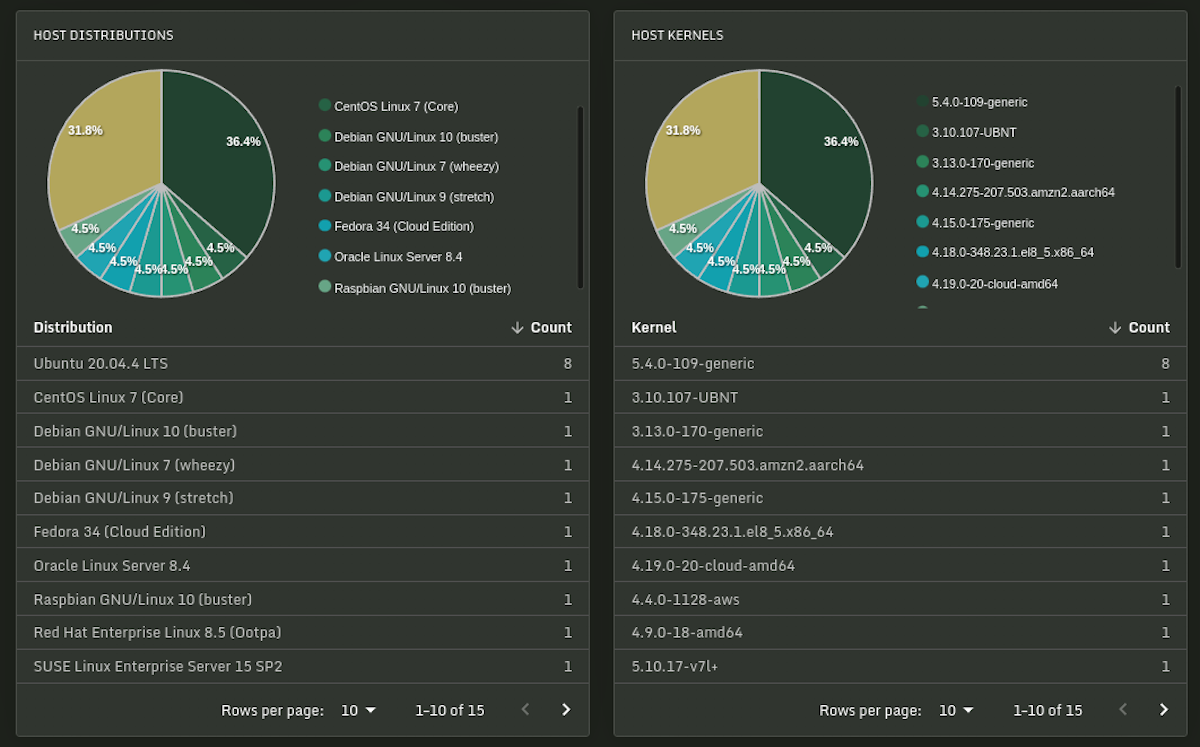
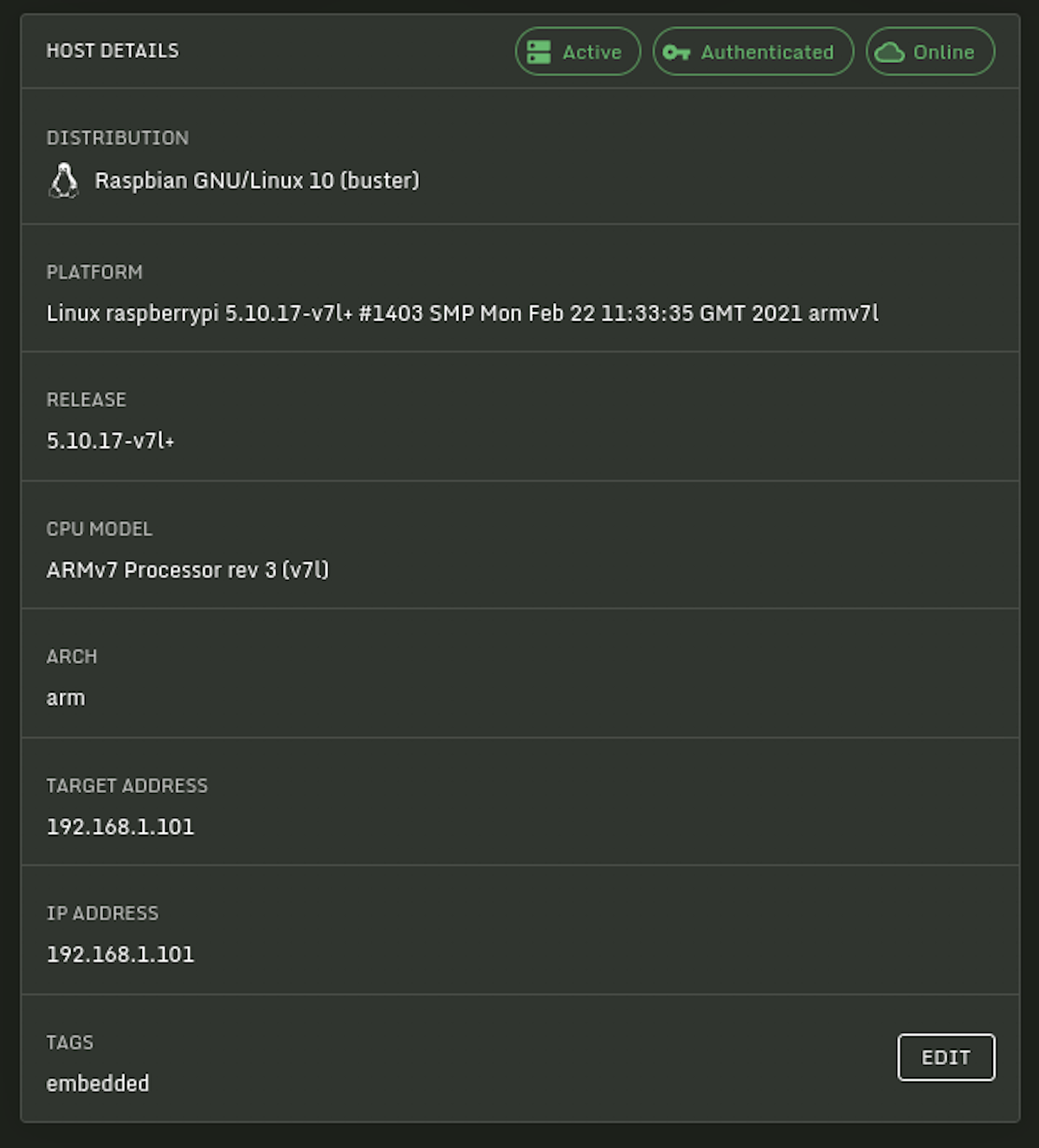
Unmonitored Linux is Dangerous
We like to say: "Sandfly is where agents can't be." This is certainly the case with embedded devices more than ever. Embedded devices must be monitored and Sandfly can help.
We are not surprised by the findings detailing targeted attacks against embedded Linux infrastructure. These devices are notoriously unmonitored and unpatched. They represent a juicy target for exploitation.
We strongly urge all customers to monitor these devices continuously, just as you do your core server infrastructure. A small embedded device can cause big trouble if left alone!