Sandfly 1.4.4 – Mind your PIDness
Sandfly 1.4.4 Update
Sandfly 1.4.4 is now released. We have added some new sandflies and broken out an older one to be more granular.
Feature list:
Sandflies to flag running processes under hidden subdirectories.
Sandflies to detect malicious PID files broken out into separate components.
Fixed a bug in the UI that was not allowing confirmation dialogs to show up without refreshing the screen.
Mind your PIDness
Yeah, it’s a bad pun but we couldn’t resist. Sandfly has features to detect malicious entries under the Linux /var/run directory targeting Process ID (PID) files. We have taken these checks and broken them out into separate components. This allows users to whitelist particular ones if they are causing a rare false alarm instead of needing to disable the entire set.
The /var/run (or /run) directory is targeted by malware on Linux. This directory is usually found across all Linux installs so it’s a handy place to do a variety of malicious things such as:
Hide executable binaries disguised as a .pid file.
Hold stolen data for later exfiltration off the host disguised as a .pid file.
Hold configuration data for malware to help with persistence inside a .pid file.
PID files under /var/run should usually contain the process number that is running (e.g. 1427, 3342, etc.). Sometimes we’ve seen PID files contain an extra line for a command that is running, but this is unusual. Mostly though if these files are holding data that isn’t a simple number value, is too large, or contains evidence it’s encrypted or a binary, then we want to alert you.
We now have the previous Sandfly PID check broken broken out into the following sandflies:
sandfly_file_suspicious_run_pid_binary – Checks for PID files that are actually Linux executable binaries. You should never see this.
sandfly_file_suspicious_run_pid_encrypted – Checks for PID files that appear to contain high entropy data indicating it may be encrypted. Malware can store stolen data in an encrypted form in PID files before data exfiltration.
sandfly_file_suspicious_run_pid_not_integer – Checks for PID files that are not simply an integer value. It is possible that a PID file may contain more than an integer, but it’s not common.
sandfly_file_suspicious_run_pid_too_big – Checks for PID files that are simply too large. Large PID files can be used to hold configuration or stolen data waiting for data exfiltration.
Processes Running from a Hidden Sub-Directory
Next we added a new class of sandfly to flag processes that are running from a hidden sub-directory anywhere in their path. For instance:
/var/tmp/.ICE-unix/
This directory appears to be normal and is found on many Linux hosts by default. But any kind of process running from this or other hidden directories is extremely suspicious in general. Why are you hiding the directory that is running a supposedly legitimate system process anyway? This is a favorite tactic of malware, especially cryptominers that we’ve been seeing a lot lately. Also it’s used by various Linux worms and rootkits.
What it looks like:
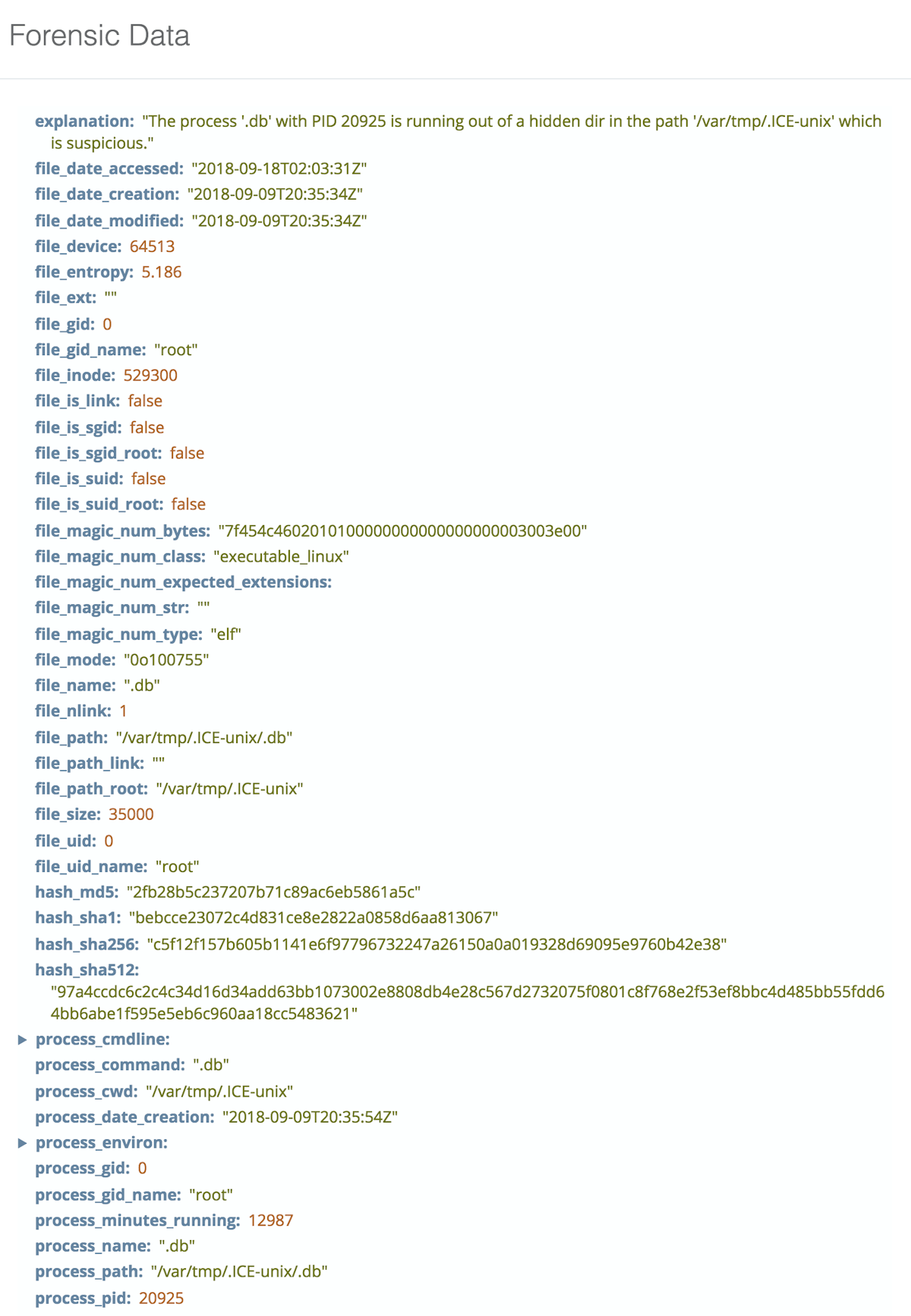
We also added in a sandfly to help incident responders that will flag processes running from a hidden directory anywhere on the system. This sandfly has extremely low chance of false alarms in general, but we’ve see a couple isolated cases so we’ve made it an incident response sandfly to be run manually as a result. This is a good check to run as an incident responder to quickly catch any malware using this tactic.
The new sandfly names are the following:
sandfly_process_running_from_hidden_bin_dir – Flags processes running from a hidden directory under common system binary directories.
sandfly_process_running_from_hidden_lib_dir – Flags processes running from a hidden directory under common system library directories.
sandfly_process_running_from_hidden_usr_dir – Flags processes running from a hidden directory under /usr directories.
sandfly_process_running_from_hidden_dev_dir – Flags processes running from a hidden directory under /dev directories.
sandfly_process_running_from_hidden_system_dir – Flags processes running from a hidden directory under system directories like /boot, /lost+found.
sandfly_process_running_from_hidden_tmp_dir – Flags processes running from a hidden directory under tmp directories.
sandfly_process_running_from_hidden_etc_dir – Flags processes running from a hidden directory under /etc directories.
sandfly_process_running_from_hidden_var_dir – Flags processes running from a hidden directory under /var directories.
sandfly_process_running_from_hidden_root_dir – Flags processes running from a hidden directory under the top level / directory.
sandfly_process_running_from_hidden_dir_anywhere – Flags processes running from a hidden directory anywhere on the system.
Upgrading Is Easy
We recommend you upgrade to the latest version to take advantage of these new features.
Upgrading Sandfly is very easy with our included scripts. Please read the instructions here:
Thank you for using Sandfly.