Linux File Masquerading and Malicious PIDs – Sandfly 1.2.6 Update
Sandfly 1.2.6 Released
This version of Sandfly has many internal performance improvements. Some sandfly checks have been sped up over 50%. We have also added a variety of new sandfly checks, some of which are outlined below.
Malicious PID Files
Sandfly now looks directly for Process ID (PID) files under /run and /var/run that are suspicious or likely malicious. On Linux, the PID files normally hold the process ID only which should just be an integer value. This is used by various programs to track previous copies that are running, to help clean up stale data, and manage other tasks.
However, many pieces of malware use the /run and /var/run areas for holding data, executables, and other tasks. We have also seen exploit code and adversary tactics use these areas for similar purposes. Sandfly has always checked these areas for problems, but now we are being very direct and analyzing the PID files themselves for the following threats:
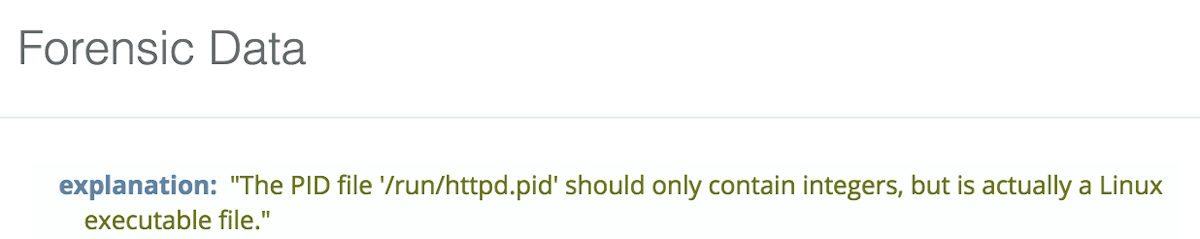
A PID file that is really an executable.
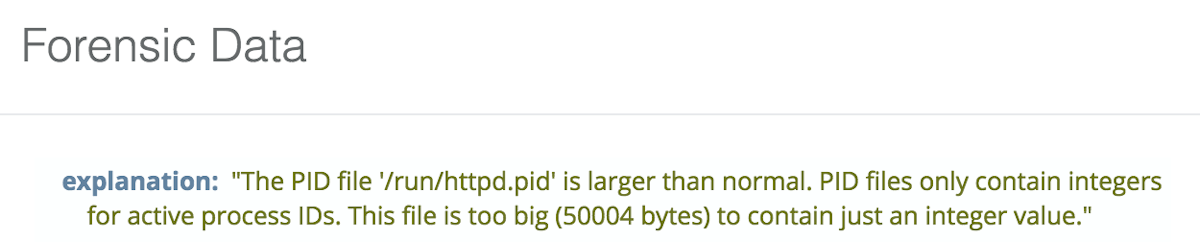
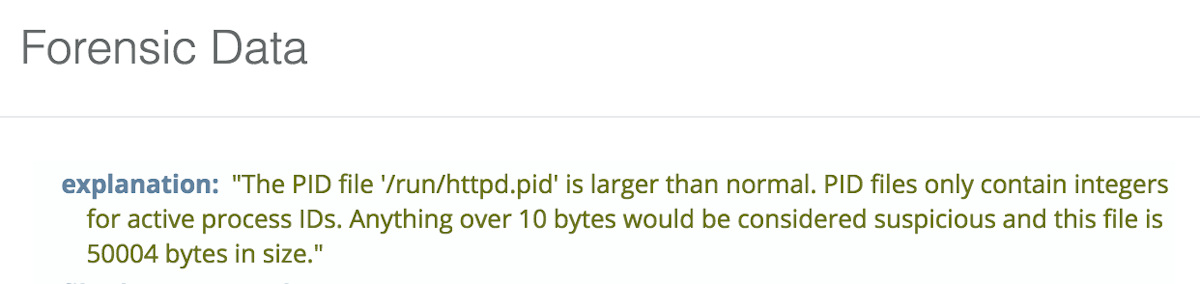
A PID file that is too large to hold just a PID integer value.
A PID file that is not an integer value.
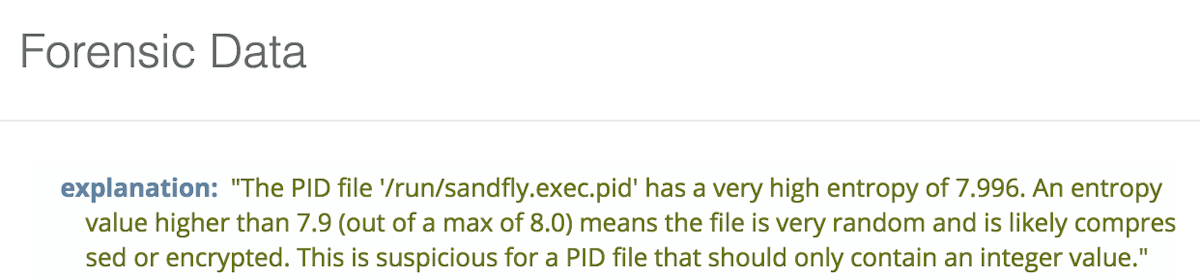
A PID file that has very high entropy indicating it may be holding encrypted data.
The above four areas can catch a variety of common and uncommon attacks that try to hide their activity as a system PID file. For instance, we have seen some attack methods using PID files to store captured data, and even encrypt this data. This sandfly can find that kind of activity. We also will flag malware or other malicious binaries trying to reside in this directory to hide or remain persistent by acting like a legitimate PID file.
Some examples of what Sandfly may detect are below:
Enhanced File Masquerading Detection
Building on the ability to detect masquerading files, we tuned our sandfly modules to be more specific in flagging files that are really Linux executables trying to hide by pretending to be another file type. For instance, a file called index.html may go unnoticed with the html extension, but in reality it could be a malicious binary hiding under your nose.
Sandfly checks files with common file extensions trying to hide the fact that they are actually executables in critical system areas. This is very effective in spotting known and unknown malware trying to hide using this tactic.
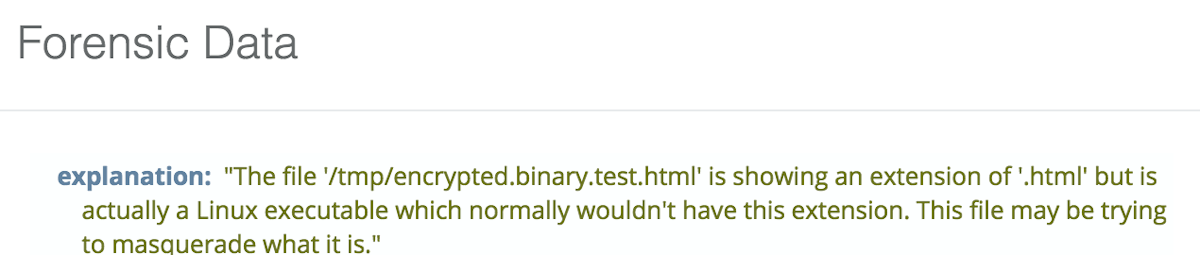
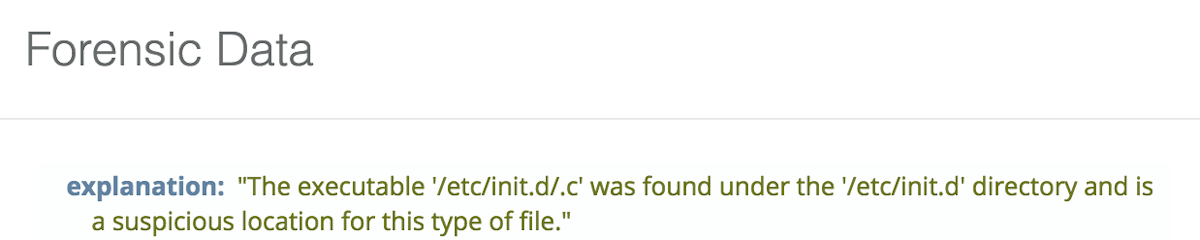
Executable In /etc Detection Updated
We have changed how we check for executable files under /etc to target high risk areas where system startup scripts reside. Executable files in areas such as /etc/init.d or any of the rc*.d directories is very suspicious behavior and we search for it directly now.
Recon Sandflies
There are special sandfly checks in the product under the “Recon” label. These sandflies were always designed only to be used for incident response because they do a very deep check for problems and may have false alarms as well as higher system impacts.
Unfortunately, the way we made them available in the UI was confusing. We have pulled these for now and they will be re-introduced in the UI update being planned now. The updates will include additional sandfly checks that can spot a variety of problems for incident response teams.
More Coming
We have many other sandfly investigation modules in the works. If you want to try out Sandfly to help protect your Linux systems, please contact us.