Linux Stealth Rootkit Malware with EDR Evasion
Recently, Sandfly was contacted to investigate an incident involving a novel piece of Linux stealth malware. What made this malware interesting is it deployed a full stealth rootkit to hide itself, and in so doing was able to evade a market leading Endpoint Detection and Response (EDR) product. The malware appeared to be focused on cryptomining, but also had SSH bruteforce and likely backdoor capability. It's not unreasonable to assume the framework could be used at some point to also deploy ransomware features if desired.
Stealth Malware Breach Suspected
The customer reported a machine acting strangely and felt that it had been compromised even though their EDR solution was not able to see the activity. During an initial triage the security team reported that some files could not be viewed (e.g. SSH authorized_keys) and other symptoms were happening indicating the host was trying to hide something.
Running Sandfly against the target showed the system had big problems with dozens of alerts. We found suspicious binaries during the incident and only one AV vendor at the time had any indication that it was malicious in VirusTotal:
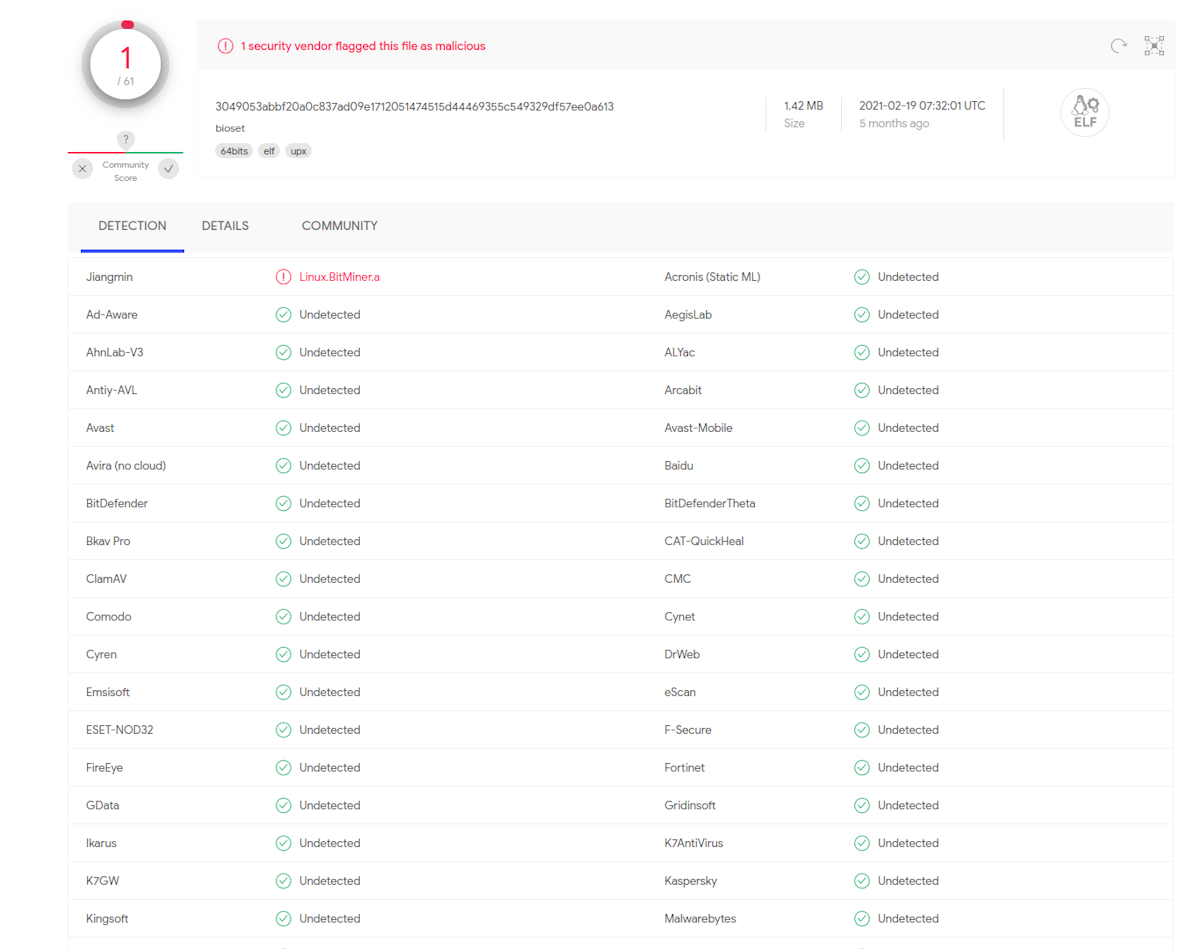
The Sandfly console though showed the following:
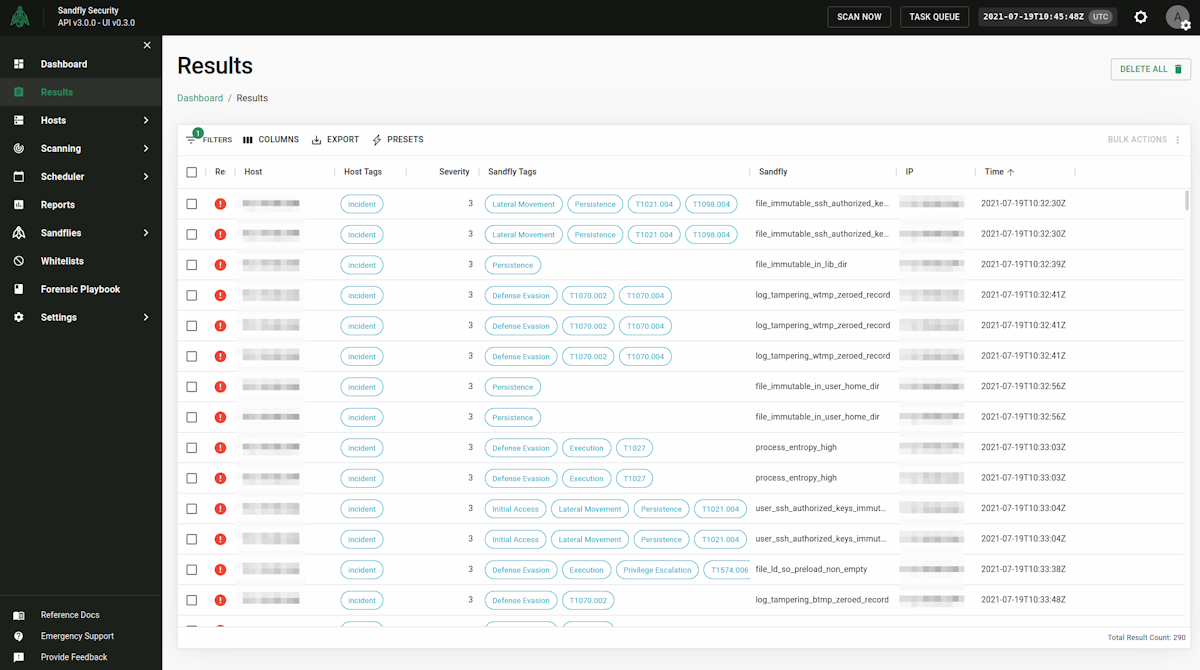
What exactly was the malware doing?
Hiding processes.
Using high entropy packed/encrypted binaries to mask contents.
Immutable process binaries for persistence.
Immutable root user SSH authorized_keys file with new key added for persistence.
Immutable config files under /etc directory.
Immutable and hidden system library file.
Tampered /etc/ld.so.preload with malicious library path.
Processes with watchdog features to restart themselves if killed.
Tampered files hidden from system commands like ls, cat, strings and lsof.
Open network connection to command and control server.
SSH bruteforcer to spread automatically.
Complete evasion from a Linux EDR solution (not Sandfly!).
Overall, this malware was a well executed stealth rootkit and payload. It was effective at hiding from observation and as stated above, evaded an EDR product. The SSH bruteforcer was aggressive in scanning and effective at finding new hosts to infect.
Linux LD_PRELOAD Stealth Rootkit and Packed Binaries
The admins suspected a rootkit was present, but standard system tools like ps, top or lsof were not showing everything. This indicates a Linux stealth rootkit was in play. There are two main types of rootkits on Linux: Loadable Kernel Module (LKM) or LD_PRELOAD style. We wanted to figure out if we were dealing with one of these and that would let us know the next step.
After running Sandfly, the first thing we found were a couple suspicious packed/encrypted binaries running called bioset and kthreadd. The files appeared to be packed with the popular tool UPX. Packing is a way to compress a binary to save space. However, in actual use it's a way to make malicious binary detection and reverse engineering harder in our experience. A packed binary on Linux is 99% of the time malicious and should be immediately investigated. Trust us. The problem is so bad we even released a free tool to help you scan your system for any packed binaries (sandfly-filescan).
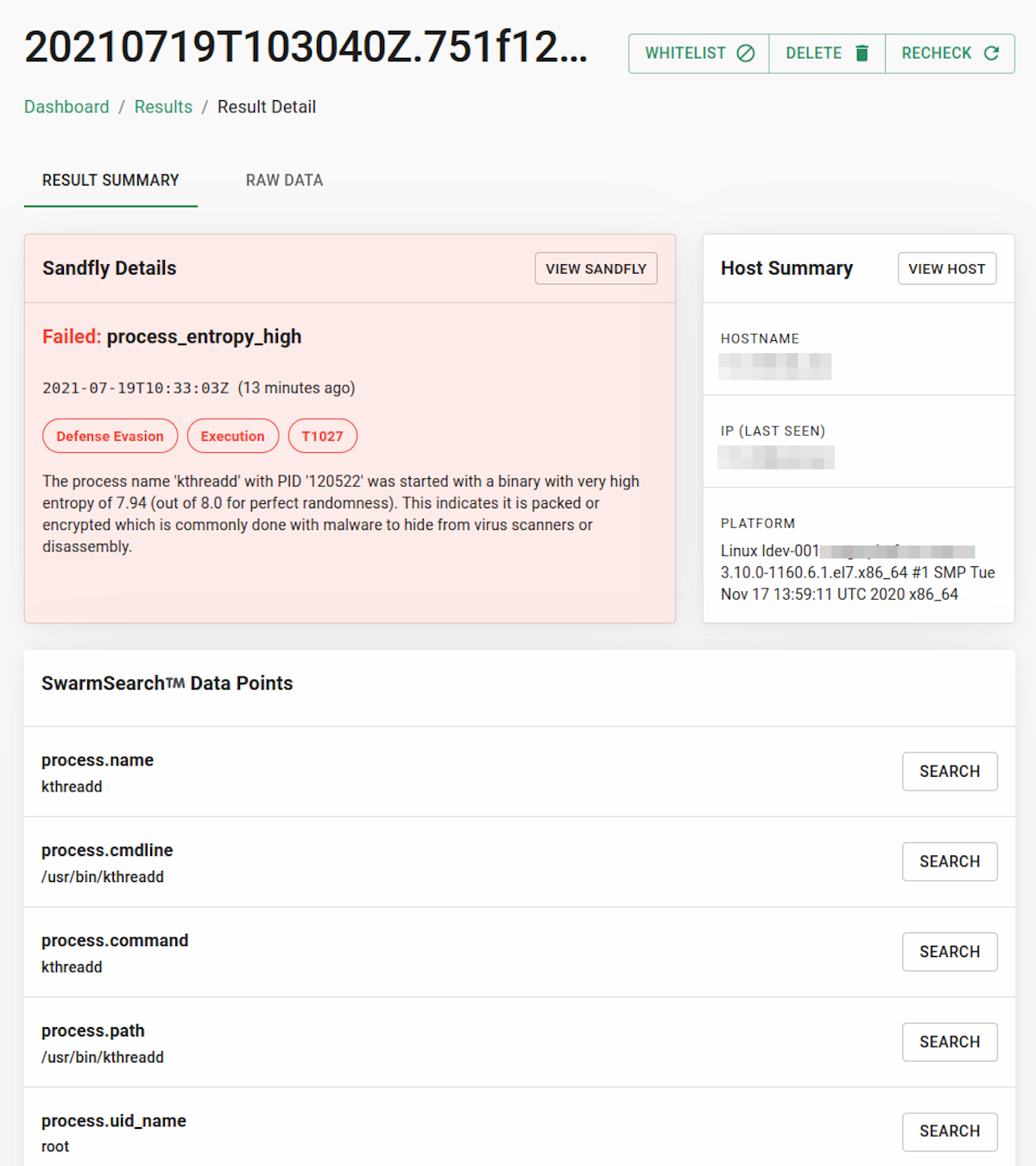
The binaries were also running with immutable permissions on the filesystem to prevent removal:
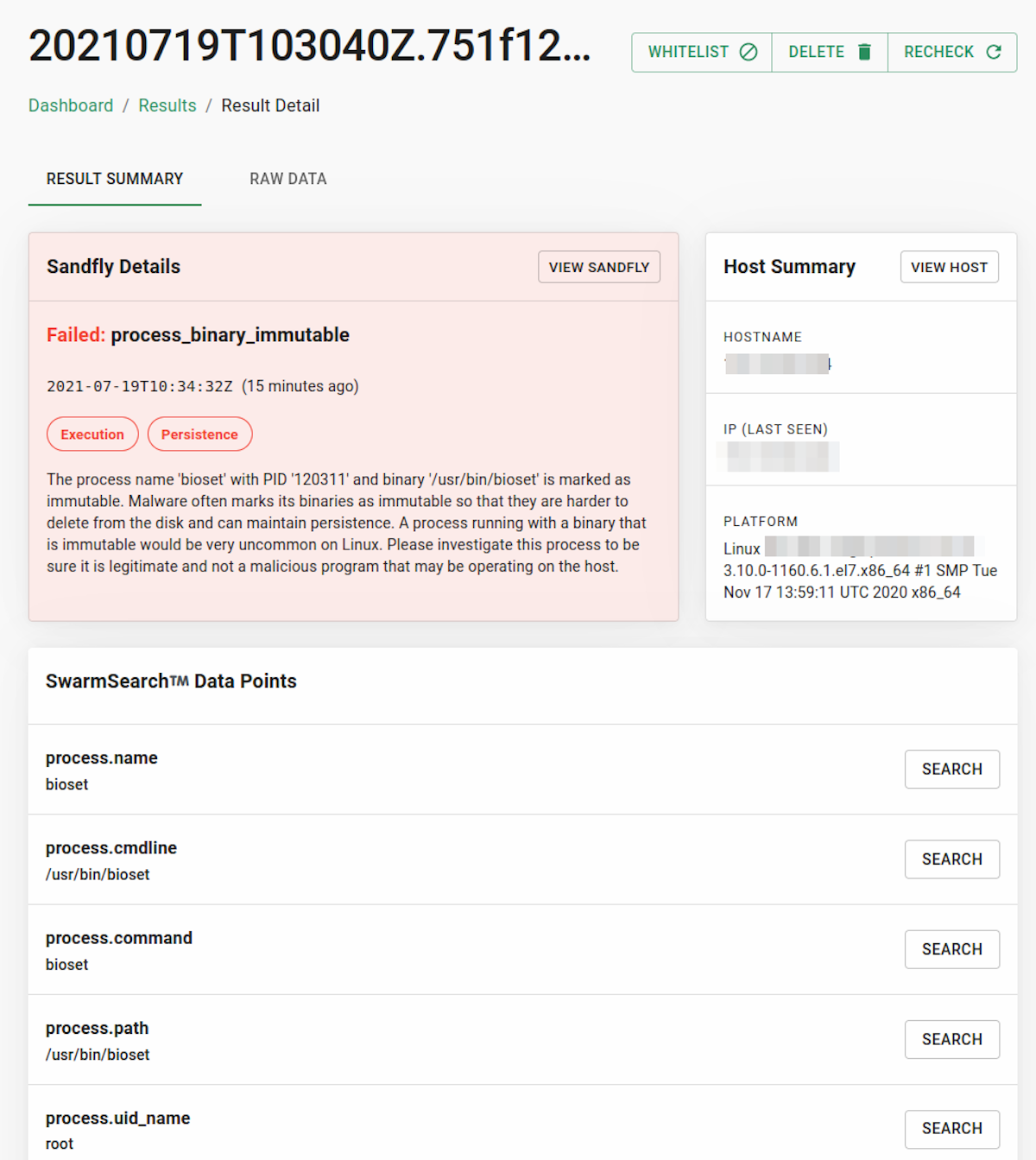
Now although they sound scary, stealth rootkits are usually easy to decloak if you know where to look (also using our free tool sandfly-processdecloak). In this case we used Sandfly as it can decloak these issues for us. An alert also stood out with processes that had active open connections to /etc/ld.so.preload on the system.
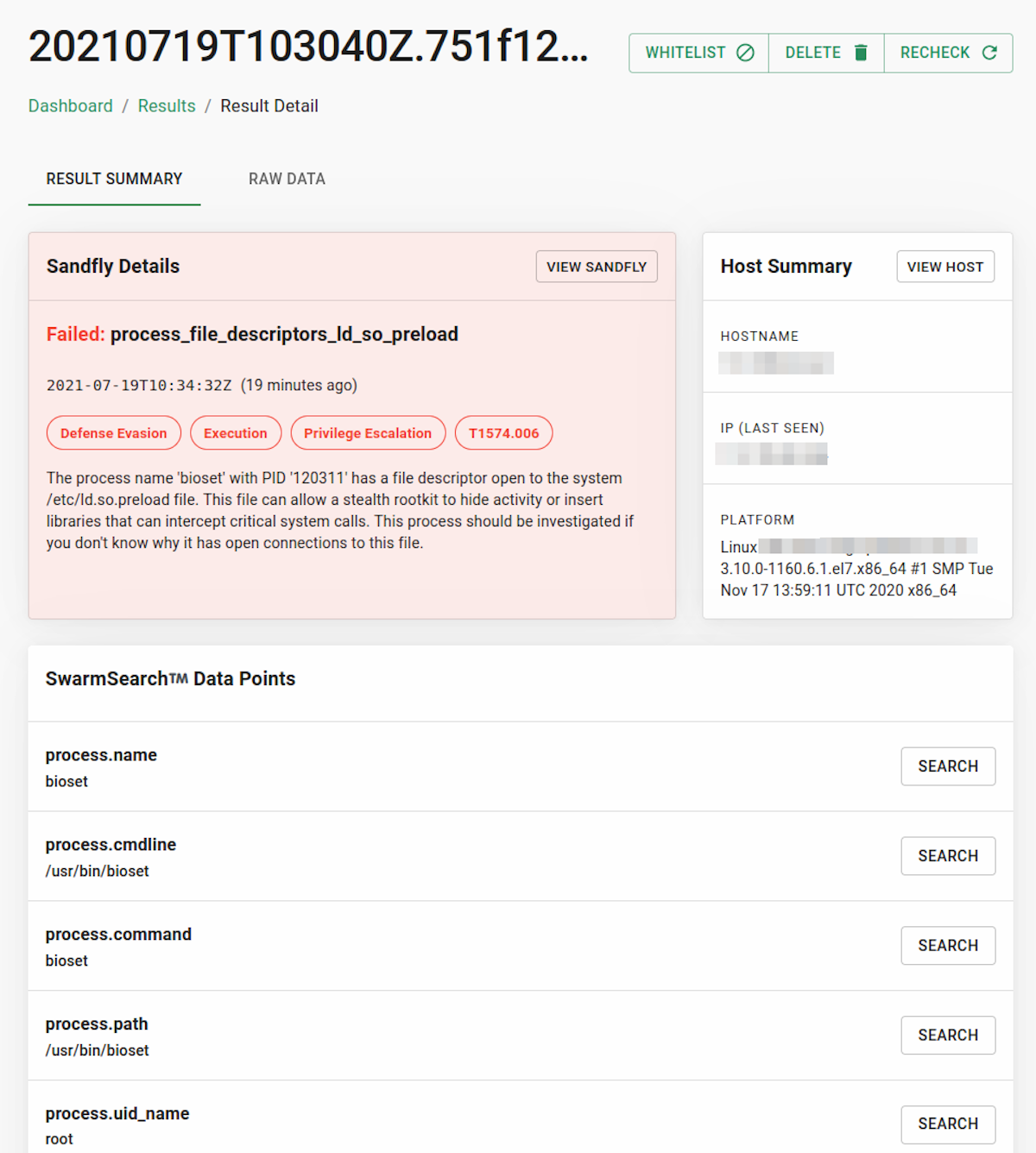
Sandfly's forensic data shows that an active file descriptor to /etc/ld.so.preload is in fact being held open by this process to protect it from alteration or removal.
Processes with an interest in /etc/ld.so.preload are important because this allows intruders to insert malicious libraries into a binary execution path. In plain terms, a malicious library can hide files, processes and directories from you if you use system tools or dynamically linked binaries. No system commands on this host can be trusted to show what is going on with this kind of rootkit present.
In fact, trying to view /etc/ld.so.preload with system commands was completely blocked by the rootkit. The file could not be viewed or even copied as it was being protected from observation or removal. At this point we are 100% certain we are dealing with a LD_PRELOAD stealth rootkit.
Decloaking a Linux Stealth Rootkit
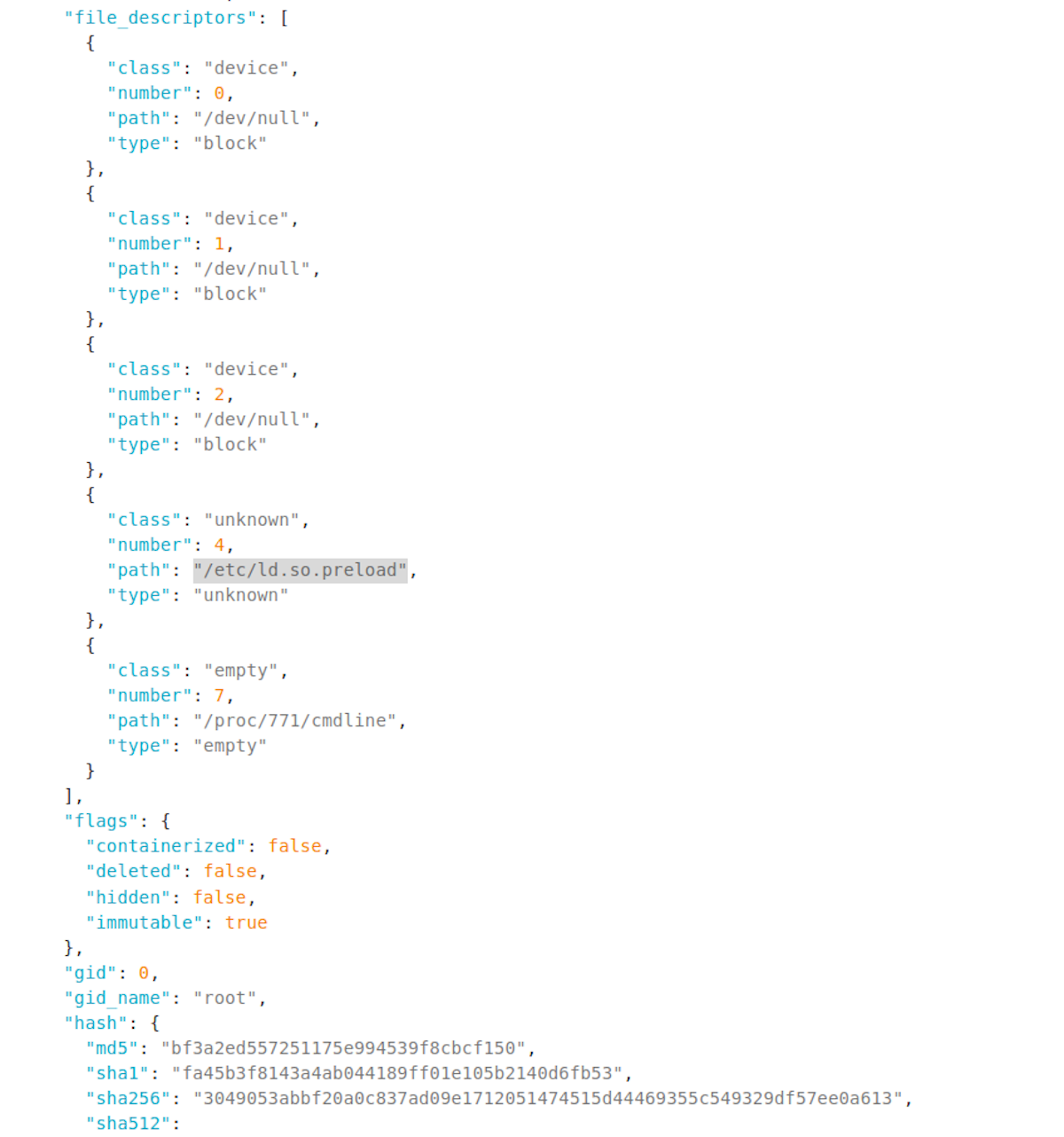
Now that we are certain that an LD_PRELOAD rootkit is in operation, we want to look into the /etc/ld.so.preload file that the malicious binary finds so interesting. Sandfly in fact flagged this file already as it was marked immutable to prevent removal which is extremely unusual on Linux.
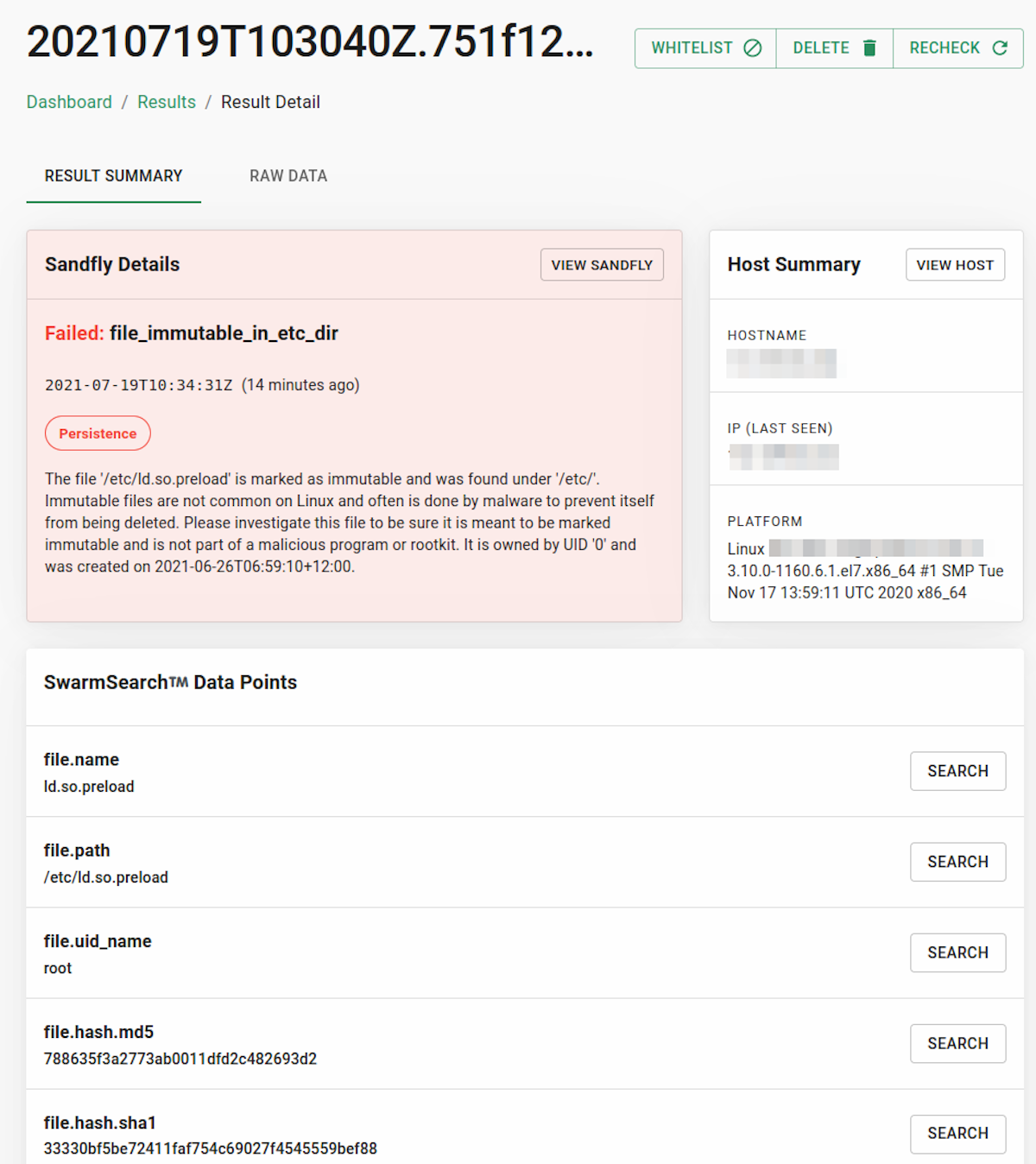
Sandfly also flagged that the file was not empty which again is not common on Linux. Although there are legitimate reasons for an LD_PRELOAD library to be used, 99% of the time a Linux host won't have anything in this file and file references there should be viewed with suspicion until proven innocent.
The system commands were not showing us the contents of the /etc/ld.so.preload file due to the rootkit, but we can use Sandfly's raw forensic data to see the decloaked data immediately:
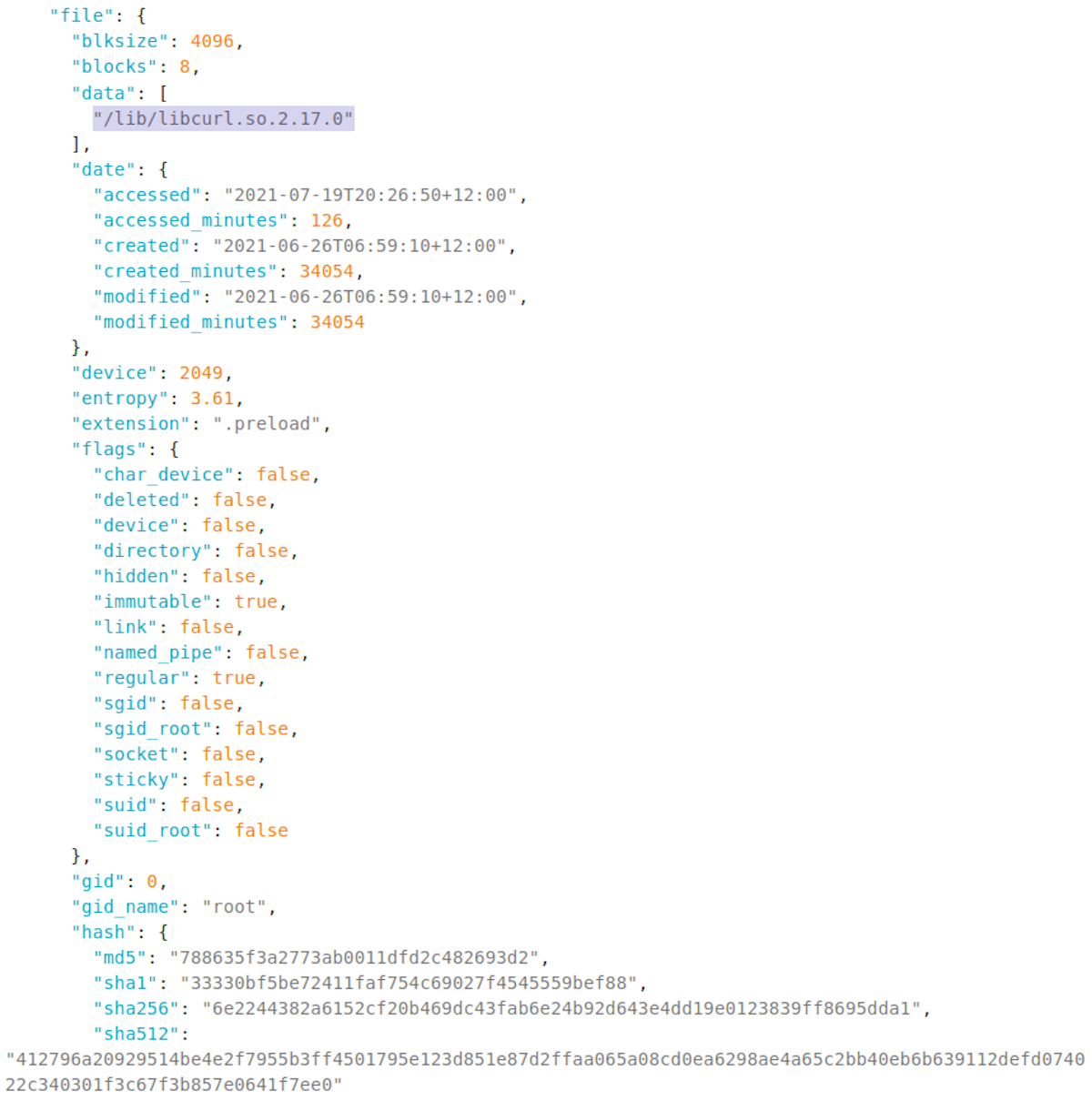
The path found in this file is a very suspiciously named /lib/libcurl.so.2.17.0 path name. If you think a reference to curl in this system file is odd, you aren't alone.
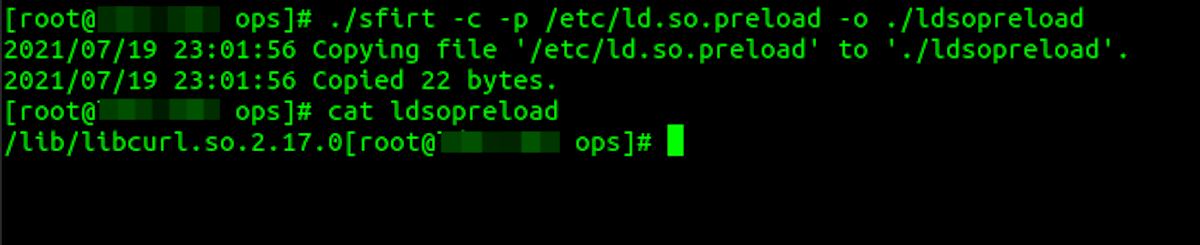
To confirm this, we used Sandfly Incident Response Tool (sfirt) we created to read the suspicious file and dump the contents from the command line even if cloaked. The file was not linefeed terminated, but you can see clearly the reference to /lib/libcurl.so.2.17.0 again confirming the forensic data above.
Inspecting Malicious LD_PRELOAD Library
Now the file of interest in the entire rootkit is /lib/libcurl.so.2.17.0. This file being referenced in /etc/ld.so.preload means that it is the one that is intercepting system calls to do the grunt work of the rootkit to hide. In this case, the file has other suspicious attributes such as being marked as immutable and also the rootkit was not allowing system commands to view it to avoid analysis.
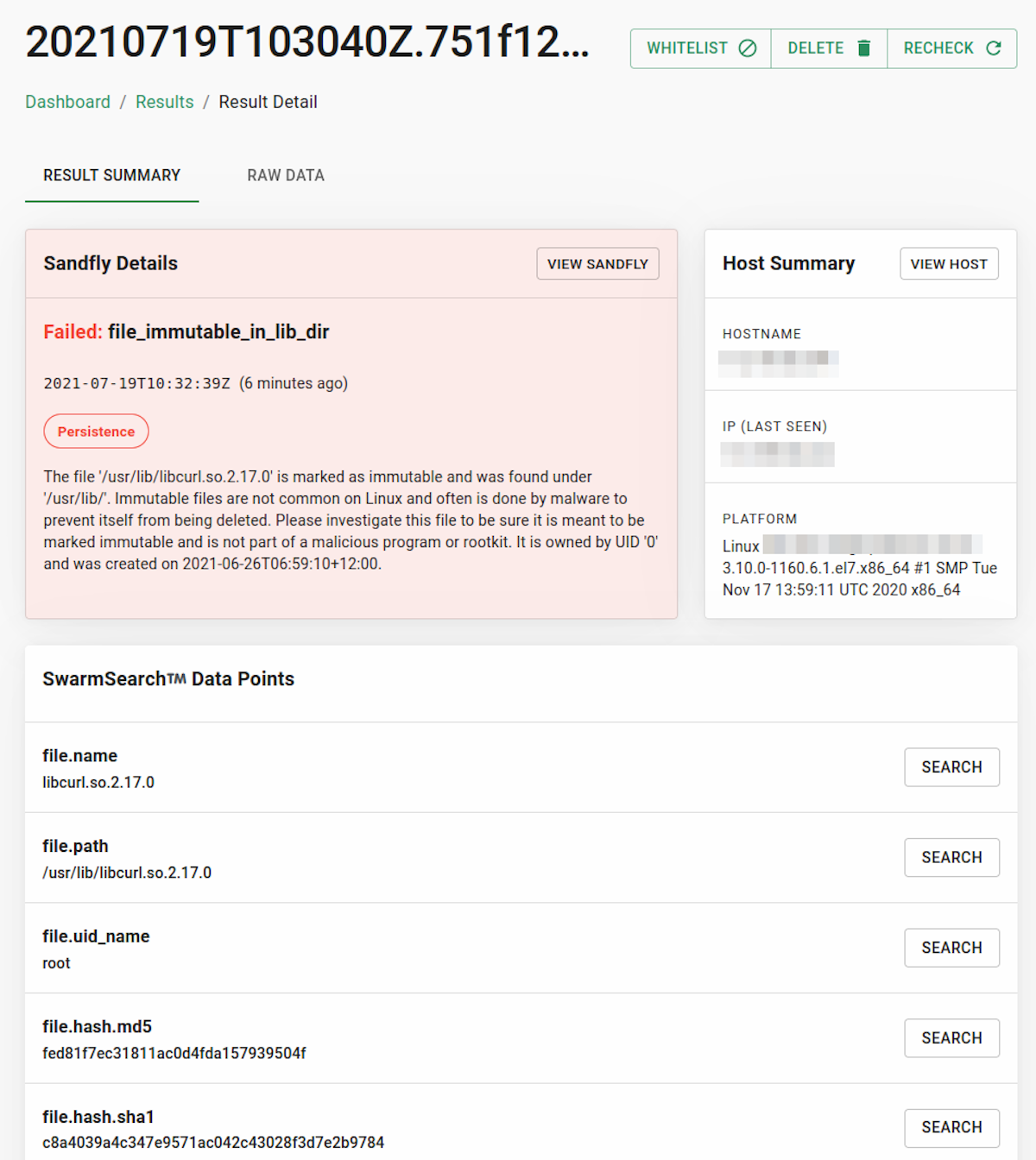
Since system commands couldn't see or look at this file as it was defending itself, we again use Sandfly's forensic view to see some clues about what it is. Here we are focused in on the magic number showing it's an ELF type file as well as cryptographic hashes which can help to search for this file on other hosts if needed:
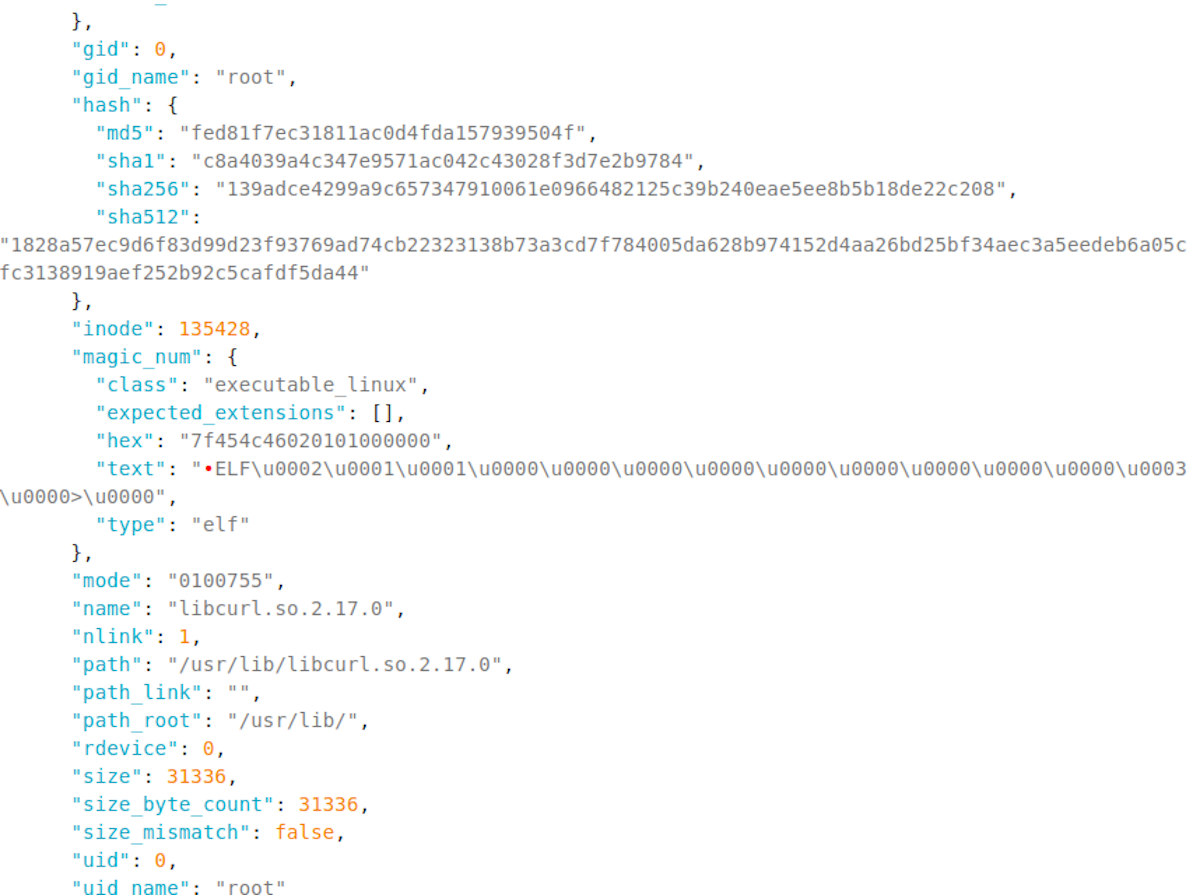
The forensic data of the malicious library is presented below from Sandfly. Note that the file was created on Jun 26th after the breach, but Sandfly was run on July 19th which is why the dates are three weeks apart.
{
"end_time": "2021-07-19T20:57:13Z",
"engine": "sandfly_engine_file",
"euid": 0,
"euid_username": "root",
"exec_seconds": 4,
"name": "file_immutable_in_lib_dir",
"output_format": "3.0",
"pid": 54929,
"results": {
"explanation": "The file '/usr/lib/libcurl.so.2.17.0' is marked as immutable and was found under '/usr/lib/'. Immutable files are not common on Linux and often is done by malware to prevent itself from being deleted. Please investigate this file to be sure it is meant to be marked immutable and is not part of a malicious program or rootkit. It is owned by UID '0' and was created on 2021-06-26T06:59:10+12:00.",
"file": {
"blksize": 4096,
"blocks": 64,
"data": null,
"date": {
"accessed": "2021-07-19T20:26:50+12:00",
"accessed_minutes": 750,
"created": "2021-06-26T06:59:10+12:00",
"created_minutes": 34678,
"modified": "2021-06-26T06:55:12+12:00",
"modified_minutes": 34682
},
"device": 2049,
"entropy": 4.31,
"extension": ".0",
"flags": {
"char_device": false,
"deleted": false,
"device": false,
"directory": false,
"hidden": false,
"immutable": true,
"link": false,
"named_pipe": false,
"regular": true,
"sgid": false,
"sgid_root": false,
"socket": false,
"sticky": false,
"suid": false,
"suid_root": false
},
"gid": 0,
"gid_name": "root",
"hash": {
"md5": "fed81f7ec31811ac0d4fda157939504f",
"sha1": "c8a4039a4c347e9571ac042c43028f3d7e2b9784",
"sha256": "139adce4299a9c657347910061e0966482125c39b240eae5ee8b5b18de22c208",
"sha512": "1828a57ec9d6f83d99d23f93769ad74cb22323138b73a3cd7f784005da628b974152d4aa26bd25bf34aec3a5eedeb6a05cfc3138919aef252b92c5cafdf5da44"
},
"inode": 135428,
"magic_num": {
"class": "executable_linux",
"expected_extensions": [],
"hex": "7f454c46020101000000",
"text": "ELF\u0002\u0001\u0001\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0003\u0000>\u0000",
"type": "elf"
},
"mode": "0100755",
"name": "libcurl.so.2.17.0",
"nlink": 1,
"path": "/usr/lib/libcurl.so.2.17.0",
"path_link": "",
"path_root": "/usr/lib/",
"rdevice": 0,
"size": 31336,
"size_byte_count": 31336,
"size_mismatch": false,
"uid": 0,
"uid_name": "root"
},
"response": {
"directory": {
"error": false
},
"file": {
"error": false
},
"log": {
"error": false
},
"process": {
"error": false,
"killed": false,
"suspended": false
},
"user": {
"error": false
}
}
},
"severity": 3,
"start_time": "2021-07-19T20:57:09Z",
"status": "alert",
"status_msg": "ok",
"tags": [
"attack.tactic.persistence",
"file"
],
"type": "file",
"uid": 0,
"uid_username": "root"
}Malicious Binary Recovery
Now that we know what kind of rootkit we have, we dive a bit into the suspicious process binaries. There were two processes called bioset and kthreadd. As discussed already, both of these processes had a keen interest in the /etc/ld.so.preload file as both had open file descriptors to it. Not only this, but the processes also had watchdog capability so if you killed the kthreadd process it would start back up again.
We did a cursory look and the kthreadd process appeared to be a generic cryptomining package. The bioset binary worked as the watchdog, SSH bruteforcer and command and control component. The binaries on the disk were protected again with immutable attributes and hidden from view with normal commands.
You can see below that normal system copy commands were not working to get the binary samples (located at /usr/bin/bioset). We again used sfirt to grab the copy and then SHA1 hash with the standard system binary once we renamed the file to something the rootkit was not protecting:
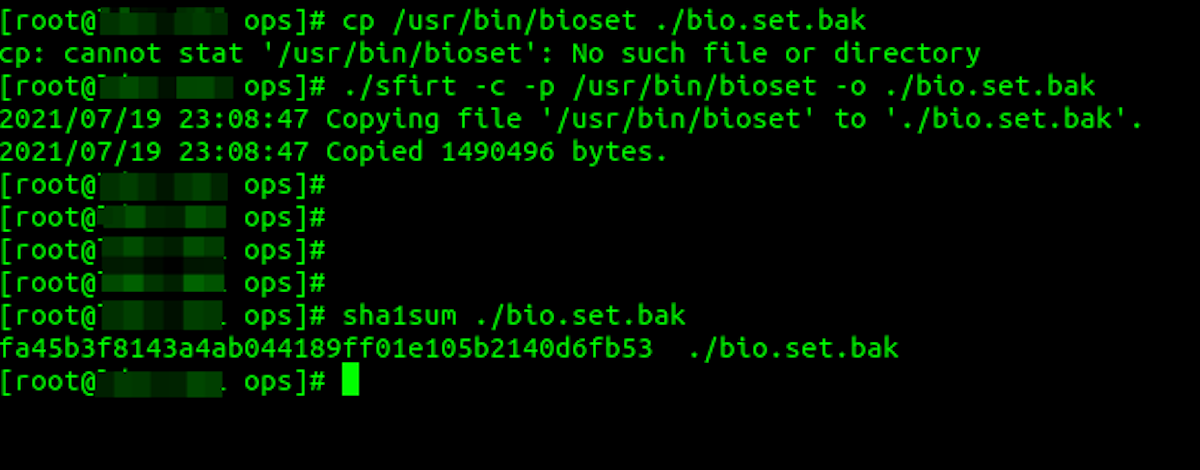
Running the hashes through VirusTotal didn't produce anything meaningful for the bioset and libcurl libraries at the time (now resolved as we submitted the samples). However the kthreadd binary did come back as a confirmed cryptominer. While this was helpful to know, the bioset binary was still a bit of a mystery. The full capability of what it could do as the main controller of the malware was not fully analyzed for this report other than to observe its involvement in SSH bruteforcing and helping the malware to spread.
While it's nice to be able to dismiss something as "only" a cryptominer, it's important to remember that a system that is compromised could have anything done to it by an attacker. It is not even unreasonable to assume that droppers that appear to be cryptomining could be left behind to throw investigators off the track of what the real intent of the attack actually was.
As this was an informal investigation, we left well enough alone as the system was already isolated and no longer a risk.
SSH Key Persistence and Odds and Ends
To wrap up the main functionality of this malware, it made other system alterations such as inserting a malicious SSH key into the root user's authorized_keys file. Details are provided in the appendix. The malware also modified miscellaneous system files like /etc/resolv.conf and had open network connections to its command and control server.
Linux EDR Evasion
One aspect of this rootkit is it was able to completely evade a well-known EDR vendor that had an agent loaded on this system. The malware itself was not specifically designed to evade EDR from what we can see, but was a side-effect of how this EDR is made. This will be covered in Part 2 of this article.
Wrap Up - Protect Your Linux Hosts
As a vendor in agentless Linux EDR, we recommend you monitor all hosts for compromise continually. Early detection is paramount to prevent minor incidents from becoming major catastrophes.
This was a well executed piece of malware. It used a simple LD_PRELOAD rootkit to hide effectively and was able to protect itself against discovery and removal to the point where it completely evaded another Linux EDR solution (covered in Part 2). In terms of malware, we actually rate this one pretty good for a cryptominer. It is showing that Linux malware authors are starting to improve their tactics and capabilities.
We hope the above shows that Linux malware is evolving rapidly and attackers are getting smarter about maintaining access and hiding their intentions. If you'd like to monitor your Linux hosts for free, please check out Sandfly and get an instant free license to do so today.
Indicators of Compromise
The following files are associated with this malware:
/etc/ld.so.preload with path to /lib/libcurl.so.2.17.0
/lib/libcurl.so.2.17.0
/usr/bin/bioset
/usr/bin/kthreadd
/root/.ssh/authorized_keys (inserts malicious key in Appendix)
Immutable flags are set on the above and/or will not be able to be read with normal system commands due to rootkit presence.
References
After our discovery we found references to variants of this malware on a Chinese site:
Analysis of "Cloud Shovel" Mining Trojan Event for a Cloud Platform Server
Appendix: Malware Forensic Data
Below are JSON forensic data from Sandfly on the malicious processes and files.
Malicious bioset Process
{
"end_time": "2021-07-19T20:59:10Z",
"engine": "sandfly_engine_process",
"euid": 0,
"euid_username": "root",
"exec_seconds": 0,
"name": "process_entropy_high",
"output_format": "3.0",
"pid": 54929,
"results": {
"explanation": "The process name 'bioset' with PID '6421' was started with a binary with very high entropy of 7.94 (out of 8.0 for perfect randomness). This indicates it is packed or encrypted which is commonly done with malware to hide from virus scanners or disassembly.",
"process": {
"binary": {
"blksize": 4096,
"blocks": 2912,
"data": null,
"date": {
"accessed": "2021-07-19T20:26:50+12:00",
"accessed_minutes": 752,
"created": "2021-06-26T06:59:10+12:00",
"created_minutes": 34679,
"modified": "2021-06-26T06:55:08+12:00",
"modified_minutes": 34683
},
"device": 2049,
"entropy": 7.94,
"extension": "",
"flags": {
"char_device": false,
"deleted": false,
"device": false,
"directory": false,
"hidden": false,
"immutable": true,
"link": false,
"named_pipe": false,
"regular": true,
"sgid": false,
"sgid_root": false,
"socket": false,
"sticky": false,
"suid": false,
"suid_root": false
},
"gid": 0,
"gid_name": "root",
"hash": {
"md5": "bf3a2ed557251175e994539f8cbcf150",
"sha1": "fa45b3f8143a4ab044189ff01e105b2140d6fb53",
"sha256": "3049053abbf20a0c837ad09e1712051474515d44469355c549329df57ee0a613",
"sha512": "e37fadfb5200f19f7e836829155b343957eae1f0588c2c6ebc3c9a78935c2ae8cdcd8a15858e70796a69ce70bc76ac3b073fbf48feb2cf990f29c414866b606d"
},
"inode": 135416,
"magic_num": {
"class": "executable_linux",
"expected_extensions": [],
"hex": "7f454c46020101030000",
"text": "ELF\u0002\u0001\u0001\u0003\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0002\u0000>\u0000",
"type": "elf"
},
"mode": "0100755",
"name": "bioset",
"nlink": 1,
"path": "/usr/bin/bioset",
"path_link": "",
"path_root": "/usr/bin/",
"rdevice": 0,
"size": 1490496,
"size_byte_count": 1490496,
"size_mismatch": false,
"uid": 0,
"uid_name": "root"
},
"cgroup": [
{
"controller_list": "freezer",
"hierarchy_id": "11",
"path": "/"
},
{
"controller_list": "devices",
"hierarchy_id": "10",
"path": "/system.slice/systemd-journald.service"
},
{
"controller_list": "cpuset",
"hierarchy_id": "9",
"path": "/"
},
{
"controller_list": "blkio",
"hierarchy_id": "8",
"path": "/system.slice/systemd-journald.service"
},
{
"controller_list": "cpuacct,cpu",
"hierarchy_id": "7",
"path": "/system.slice/systemd-journald.service"
},
{
"controller_list": "perf_event",
"hierarchy_id": "6",
"path": "/"
},
{
"controller_list": "hugetlb",
"hierarchy_id": "5",
"path": "/"
},
{
"controller_list": "pids",
"hierarchy_id": "4",
"path": "/system.slice/systemd-journald.service"
},
{
"controller_list": "net_prio,net_cls",
"hierarchy_id": "3",
"path": "/"
},
{
"controller_list": "memory",
"hierarchy_id": "2",
"path": "/system.slice/systemd-journald.service"
},
{
"controller_list": "name=systemd",
"hierarchy_id": "1",
"path": "/system.slice/systemd-journald.service"
}
],
"cmdline": "/usr/bin/bioset",
"command": "bioset",
"container": {
"id": "",
"id_short": "",
"upperdir": "",
"workingdir": ""
},
"cwd": "/",
"date": {
"created": "2021-07-19T23:53:48+12:00",
"created_minutes": 545
},
"entropy": 7.94,
"environ": [
"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin",
"PWD=/",
"LANG=en_NZ.UTF-8",
"NOTIFY_SOCKET=/run/systemd/notify",
"SHLVL=1",
"WATCHDOG_PID=471",
"WATCHDOG_USEC=180000000",
"_=/usr/bin/bioset",
""
],
"extension": "",
"file_descriptors": [
{
"class": "device",
"number": 0,
"path": "/dev/null",
"type": "block"
},
{
"class": "device",
"number": 1,
"path": "/dev/null",
"type": "block"
},
{
"class": "device",
"number": 2,
"path": "/dev/null",
"type": "block"
}
],
"flags": {
"containerized": false,
"deleted": false,
"hidden": false,
"immutable": true
},
"gid": 0,
"gid_name": "root",
"hash": {
"md5": "bf3a2ed557251175e994539f8cbcf150",
"sha1": "fa45b3f8143a4ab044189ff01e105b2140d6fb53",
"sha256": "3049053abbf20a0c837ad09e1712051474515d44469355c549329df57ee0a613",
"sha512": "e37fadfb5200f19f7e836829155b343957eae1f0588c2c6ebc3c9a78935c2ae8cdcd8a15858e70796a69ce70bc76ac3b073fbf48feb2cf990f29c414866b606d"
},
"maps": [
"00400000-00401000 r--p 00000000 00:00 0 ",
"00401000-00676000 r-xp 00000000 00:00 0 ",
"00676000-00776000 r--p 00000000 00:00 0 ",
"00776000-007ae000 rw-p 00000000 00:00 0 ",
"027a4000-027c7000 rw-p 00000000 00:00 0 [heap]",
"7f7c08000000-7f7c08029000 rw-p 00000000 00:00 0 ",
"7f7c08029000-7f7c0c000000 ---p 00000000 00:00 0 ",
"7f7c0c000000-7f7c0c029000 rw-p 00000000 00:00 0 ",
"7f7c0c029000-7f7c10000000 ---p 00000000 00:00 0 ",
"7f7c10000000-7f7c10029000 rw-p 00000000 00:00 0 ",
"7f7c10029000-7f7c14000000 ---p 00000000 00:00 0 ",
"7f7c14000000-7f7c14029000 rw-p 00000000 00:00 0 ",
"7f7c14029000-7f7c18000000 ---p 00000000 00:00 0 ",
"7f7c18000000-7f7c18029000 rw-p 00000000 00:00 0 ",
"7f7c18029000-7f7c1c000000 ---p 00000000 00:00 0 ",
"7f7c1ef76000-7f7c1ef77000 ---p 00000000 00:00 0 ",
"7f7c1ef77000-7f7c1f777000 rw-p 00000000 00:00 0 ",
"7f7c1f777000-7f7c1f778000 ---p 00000000 00:00 0 ",
"7f7c1f778000-7f7c1ff78000 rw-p 00000000 00:00 0 ",
"7f7c1ff78000-7f7c1ff79000 ---p 00000000 00:00 0 ",
"7f7c1ff79000-7f7c20779000 rw-p 00000000 00:00 0 ",
"7f7c20779000-7f7c2077a000 ---p 00000000 00:00 0 ",
"7f7c2077a000-7f7c20f7a000 rw-p 00000000 00:00 0 ",
"7f7c20f7a000-7f7c20f7b000 ---p 00000000 00:00 0 ",
"7f7c20f7b000-7f7c2177b000 rw-p 00000000 00:00 0 ",
"7f7c2177b000-7f7c2177c000 ---p 00000000 00:00 0 ",
"7f7c2177c000-7f7c21f7c000 rw-p 00000000 00:00 0 ",
"7f7c21f7c000-7f7c21f7d000 ---p 00000000 00:00 0 ",
"7f7c21f7d000-7f7c2277d000 rw-p 00000000 00:00 0 ",
"7f7c2277d000-7f7c2277e000 ---p 00000000 00:00 0 ",
"7f7c2277e000-7f7c22f7e000 rw-p 00000000 00:00 0 ",
"7f7c22f7e000-7f7c22f7f000 ---p 00000000 00:00 0 ",
"7f7c22f7f000-7f7c2377f000 rw-p 00000000 00:00 0 ",
"7f7c2377f000-7f7c23780000 ---p 00000000 00:00 0 ",
"7f7c23780000-7f7c23f80000 rw-p 00000000 00:00 0 ",
"7f7c23f80000-7f7c23f81000 ---p 00000000 00:00 0 ",
"7f7c23f81000-7f7c24781000 rw-p 00000000 00:00 0 ",
"7f7c24781000-7f7c24782000 ---p 00000000 00:00 0 ",
"7f7c24782000-7f7c24f82000 rw-p 00000000 00:00 0 ",
"7f7c24f82000-7f7c24f83000 ---p 00000000 00:00 0 ",
"7f7c24f83000-7f7c25783000 rw-p 00000000 00:00 0 ",
"7f7c25783000-7f7c25784000 ---p 00000000 00:00 0 ",
"7f7c25784000-7f7c25f84000 rw-p 00000000 00:00 0 ",
"7f7c25f84000-7f7c25f85000 ---p 00000000 00:00 0 ",
"7f7c25f85000-7f7c26785000 rw-p 00000000 00:00 0 ",
"7f7c26785000-7f7c26786000 ---p 00000000 00:00 0 ",
"7f7c26786000-7f7c26f86000 rw-p 00000000 00:00 0 ",
"7f7c26f86000-7f7c26f87000 ---p 00000000 00:00 0 ",
"7f7c26f87000-7f7c27787000 rw-p 00000000 00:00 0 ",
"7f7c27787000-7f7c27788000 ---p 00000000 00:00 0 ",
"7f7c27788000-7f7c27f88000 rw-p 00000000 00:00 0 ",
"7f7c27f88000-7f7c27f89000 ---p 00000000 00:00 0 ",
"7f7c27f89000-7f7c28789000 rw-p 00000000 00:00 0 ",
"7f7c28789000-7f7c2878a000 ---p 00000000 00:00 0 ",
"7f7c2878a000-7f7c28f8a000 rw-p 00000000 00:00 0 ",
"7f7c28f8a000-7f7c28f8b000 ---p 00000000 00:00 0 ",
"7f7c28f8b000-7f7c2978b000 rw-p 00000000 00:00 0 ",
"7f7c2978b000-7f7c2978c000 ---p 00000000 00:00 0 ",
"7f7c2978c000-7f7c29f8c000 rw-p 00000000 00:00 0 ",
"7f7c29f8c000-7f7c29f8d000 ---p 00000000 00:00 0 ",
"7f7c29f8d000-7f7c2a78d000 rw-p 00000000 00:00 0 ",
"7f7c2a78d000-7f7c2a78e000 ---p 00000000 00:00 0 ",
"7f7c2a78e000-7f7c2af8e000 rw-p 00000000 00:00 0 ",
"7f7c2af8e000-7f7c2af8f000 ---p 00000000 00:00 0 ",
"7f7c2af8f000-7f7c2b78f000 rw-p 00000000 00:00 0 ",
"7f7c2b78f000-7f7c2b790000 ---p 00000000 00:00 0 ",
"7f7c2b790000-7f7c2bf90000 rw-p 00000000 00:00 0 ",
"7f7c2bf90000-7f7c2bf91000 ---p 00000000 00:00 0 ",
"7f7c2bf91000-7f7c2c791000 rw-p 00000000 00:00 0 ",
"7f7c2c791000-7f7c2c792000 ---p 00000000 00:00 0 ",
"7f7c2c792000-7f7c2cf92000 rw-p 00000000 00:00 0 ",
"7f7c2cf92000-7f7c2cf93000 ---p 00000000 00:00 0 ",
"7f7c2cf93000-7f7c2d793000 rw-p 00000000 00:00 0 ",
"7f7c2d793000-7f7c2d794000 ---p 00000000 00:00 0 ",
"7f7c2d794000-7f7c2df94000 rw-p 00000000 00:00 0 ",
"7f7c2df94000-7f7c2df95000 ---p 00000000 00:00 0 ",
"7f7c2df95000-7f7c2e795000 rw-p 00000000 00:00 0 ",
"7f7c2e795000-7f7c2e796000 ---p 00000000 00:00 0 ",
"7f7c2e796000-7f7c2ef96000 rw-p 00000000 00:00 0 ",
"7f7c2ef96000-7f7c2ef97000 ---p 00000000 00:00 0 ",
"7f7c2ef97000-7f7c2f797000 rw-p 00000000 00:00 0 ",
"7f7c2f797000-7f7c2f798000 ---p 00000000 00:00 0 ",
"7f7c2f798000-7f7c2ff98000 rw-p 00000000 00:00 0 ",
"7f7c2ff98000-7f7c2ff99000 ---p 00000000 00:00 0 ",
"7f7c2ff99000-7f7c30799000 rw-p 00000000 00:00 0 ",
"7f7c30799000-7f7c3079a000 ---p 00000000 00:00 0 ",
"7f7c3079a000-7f7c30f9a000 rw-p 00000000 00:00 0 ",
"7f7c30f9a000-7f7c30f9b000 ---p 00000000 00:00 0 ",
"7f7c30f9b000-7f7c3179b000 rw-p 00000000 00:00 0 ",
"7f7c3179b000-7f7c3179c000 ---p 00000000 00:00 0 ",
"7f7c3179c000-7f7c31f9c000 rw-p 00000000 00:00 0 ",
"7f7c31f9c000-7f7c31f9d000 ---p 00000000 00:00 0 ",
"7f7c31f9d000-7f7c3279d000 rw-p 00000000 00:00 0 ",
"7f7c3279d000-7f7c3279e000 ---p 00000000 00:00 0 ",
"7f7c3279e000-7f7c32f9e000 rw-p 00000000 00:00 0 ",
"7f7c32f9e000-7f7c32f9f000 ---p 00000000 00:00 0 ",
"7f7c32f9f000-7f7c3379f000 rw-p 00000000 00:00 0 ",
"7f7c3379f000-7f7c337a0000 ---p 00000000 00:00 0 ",
"7f7c337a0000-7f7c33fa0000 rw-p 00000000 00:00 0 ",
"7f7c33fa0000-7f7c33fa1000 ---p 00000000 00:00 0 ",
"7f7c33fa1000-7f7c347a1000 rw-p 00000000 00:00 0 ",
"7f7c347a1000-7f7c347a2000 ---p 00000000 00:00 0 ",
"7f7c347a2000-7f7c34fa2000 rw-p 00000000 00:00 0 ",
"7f7c34fa2000-7f7c34fa3000 ---p 00000000 00:00 0 ",
"7f7c34fa3000-7f7c357a3000 rw-p 00000000 00:00 0 ",
"7f7c357a3000-7f7c357a4000 ---p 00000000 00:00 0 ",
"7f7c357a4000-7f7c35fa4000 rw-p 00000000 00:00 0 ",
"7f7c35fa4000-7f7c35fa5000 ---p 00000000 00:00 0 ",
"7f7c35fa5000-7f7c367a5000 rw-p 00000000 00:00 0 ",
"7f7c367a5000-7f7c367a6000 ---p 00000000 00:00 0 ",
"7f7c367a6000-7f7c36fa6000 rw-p 00000000 00:00 0 ",
"7f7c36fa6000-7f7c36fa7000 ---p 00000000 00:00 0 ",
"7f7c36fa7000-7f7c377a7000 rw-p 00000000 00:00 0 ",
"7f7c377a7000-7f7c377a8000 ---p 00000000 00:00 0 ",
"7f7c377a8000-7f7c37fa8000 rw-p 00000000 00:00 0 ",
"7f7c37fa8000-7f7c37fa9000 ---p 00000000 00:00 0 ",
"7f7c37fa9000-7f7c387a9000 rw-p 00000000 00:00 0 ",
"7f7c387a9000-7f7c387aa000 ---p 00000000 00:00 0 ",
"7f7c387aa000-7f7c38faa000 rw-p 00000000 00:00 0 ",
"7f7c38faa000-7f7c38fab000 ---p 00000000 00:00 0 ",
"7f7c38fab000-7f7c397ab000 rw-p 00000000 00:00 0 ",
"7f7c397ab000-7f7c397ac000 ---p 00000000 00:00 0 ",
"7f7c397ac000-7f7c39fac000 rw-p 00000000 00:00 0 ",
"7f7c39fac000-7f7c39fad000 ---p 00000000 00:00 0 ",
"7f7c39fad000-7f7c3a7ad000 rw-p 00000000 00:00 0 ",
"7f7c3a7ad000-7f7c3a7ae000 ---p 00000000 00:00 0 ",
"7f7c3a7ae000-7f7c3afae000 rw-p 00000000 00:00 0 ",
"7f7c3afae000-7f7c3afaf000 ---p 00000000 00:00 0 ",
"7f7c3afaf000-7f7c3b7af000 rw-p 00000000 00:00 0 ",
"7f7c3b7af000-7f7c3b7b0000 ---p 00000000 00:00 0 ",
"7f7c3b7b0000-7f7c3bfb0000 rw-p 00000000 00:00 0 ",
"7f7c3bfb0000-7f7c3bfb1000 ---p 00000000 00:00 0 ",
"7f7c3bfb1000-7f7c3c7b1000 rw-p 00000000 00:00 0 ",
"7f7c3c7b1000-7f7c3c7b2000 ---p 00000000 00:00 0 ",
"7f7c3c7b2000-7f7c3cfb2000 rw-p 00000000 00:00 0 ",
"7f7c3cfb2000-7f7c3cfb3000 ---p 00000000 00:00 0 ",
"7f7c3cfb3000-7f7c3d7b3000 rw-p 00000000 00:00 0 ",
"7f7c3d7b3000-7f7c3d7b4000 ---p 00000000 00:00 0 ",
"7f7c3d7b4000-7f7c3dfb4000 rw-p 00000000 00:00 0 ",
"7f7c3dfb4000-7f7c3dfb5000 ---p 00000000 00:00 0 ",
"7f7c3dfb5000-7f7c3e7b5000 rw-p 00000000 00:00 0 ",
"7f7c3e7b5000-7f7c3e7b6000 ---p 00000000 00:00 0 ",
"7f7c3e7b6000-7f7c3efb6000 rw-p 00000000 00:00 0 ",
"7f7c3efb6000-7f7c3efb7000 ---p 00000000 00:00 0 ",
"7f7c3efb7000-7f7c3f7b7000 rw-p 00000000 00:00 0 ",
"7f7c3f7b7000-7f7c3f7b8000 ---p 00000000 00:00 0 ",
"7f7c3f7b8000-7f7c3ffb8000 rw-p 00000000 00:00 0 ",
"7f7c3ffb8000-7f7c3ffb9000 ---p 00000000 00:00 0 ",
"7f7c3ffb9000-7f7c407b9000 rw-p 00000000 00:00 0 ",
"7f7c407b9000-7f7c407ba000 ---p 00000000 00:00 0 ",
"7f7c407ba000-7f7c40fba000 rw-p 00000000 00:00 0 ",
"7f7c54000000-7f7c54029000 rw-p 00000000 00:00 0 ",
"7f7c54029000-7f7c58000000 ---p 00000000 00:00 0 ",
"7f7c5c000000-7f7c5c029000 rw-p 00000000 00:00 0 ",
"7f7c5c029000-7f7c60000000 ---p 00000000 00:00 0 ",
"7f7c60000000-7f7c60029000 rw-p 00000000 00:00 0 ",
"7f7c60029000-7f7c64000000 ---p 00000000 00:00 0 ",
"7f7c64000000-7f7c64029000 rw-p 00000000 00:00 0 ",
"7f7c64029000-7f7c68000000 ---p 00000000 00:00 0 ",
"7f7c68000000-7f7c68029000 rw-p 00000000 00:00 0 ",
"7f7c68029000-7f7c6c000000 ---p 00000000 00:00 0 ",
"7f7c6c000000-7f7c6c029000 rw-p 00000000 00:00 0 ",
"7f7c6c029000-7f7c70000000 ---p 00000000 00:00 0 ",
"7f7c70000000-7f7c70029000 rw-p 00000000 00:00 0 ",
"7f7c70029000-7f7c74000000 ---p 00000000 00:00 0 ",
"7f7c74000000-7f7c74021000 rw-p 00000000 00:00 0 ",
"7f7c74021000-7f7c78000000 ---p 00000000 00:00 0 ",
"7f7c7b46e000-7f7c7b46f000 ---p 00000000 00:00 0 ",
"7f7c7b46f000-7f7c7bc6f000 rw-p 00000000 00:00 0 ",
"7f7c7bc6f000-7f7c7bc70000 ---p 00000000 00:00 0 ",
"7f7c7bc70000-7f7c7c470000 rw-p 00000000 00:00 0 ",
"7f7c7c470000-7f7c7c471000 ---p 00000000 00:00 0 ",
"7f7c7c471000-7f7c7cc71000 rw-p 00000000 00:00 0 ",
"7f7c7cc71000-7f7c7cc72000 ---p 00000000 00:00 0 ",
"7f7c7cc72000-7f7c7d472000 rw-p 00000000 00:00 0 ",
"7f7c7d472000-7f7c7d473000 r--p 00000000 08:01 135416 /usr/bin/bioset",
"7ffe064e2000-7ffe06503000 rw-p 00000000 00:00 0 [stack]",
"7ffe06518000-7ffe0651a000 r-xp 00000000 00:00 0 [vdso]",
"ffffffffff600000-ffffffffff601000 r-xp 00000000 00:00 0 [vsyscall]"
],
"name": "bioset",
"network_ports": {
"established": false,
"established_num": 0,
"icmp": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"icmp6": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"listening": false,
"listening_num": 0,
"operating": false,
"raw": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"raw6": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"sctp": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"tcp": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"tcp6": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"udp": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"udp6": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
}
},
"path": "/usr/bin/bioset",
"pgid": 6421,
"pid": 6421,
"ppid": 1,
"stack": [
"hrtimer_nanosleep+0xbb/0x180",
"SyS_nanosleep+0x96/0xb0",
"system_call_fastpath+0x25/0x2a",
"0xffffffffffffffff"
],
"state": "S",
"system_uptime": "2021-07-10T14:24:17+12:00",
"uid": 0,
"uid_name": "root"
},
"response": {
"directory": {
"error": false
},
"file": {
"error": false
},
"log": {
"error": false
},
"process": {
"error": false,
"killed": false,
"suspended": false
},
"user": {
"error": false
}
}
},
"severity": 3,
"start_time": "2021-07-19T20:59:10Z",
"status": "alert",
"status_msg": "ok",
"tags": [
"attack.id.T1027",
"attack.tactic.defense_evasion",
"attack.tactic.execution",
"process"
],
"type": "process",
"uid": 0,
"uid_username": "root"
}Malicious kthreadd Process
{
"end_time": "2021-07-19T20:59:10Z",
"engine": "sandfly_engine_process",
"euid": 0,
"euid_username": "root",
"exec_seconds": 0,
"name": "process_entropy_high",
"output_format": "3.0",
"pid": 54929,
"results": {
"explanation": "The process name 'kthreadd' with PID '6572' was started with a binary with very high entropy of 7.94 (out of 8.0 for perfect randomness). This indicates it is packed or encrypted which is commonly done with malware to hide from virus scanners or disassembly.",
"process": {
"binary": {
"blksize": 4096,
"blocks": 2496,
"data": null,
"date": {
"accessed": "2021-07-19T20:26:50+12:00",
"accessed_minutes": 752,
"created": "2021-06-26T06:59:10+12:00",
"created_minutes": 34679,
"modified": "2021-06-26T06:56:58+12:00",
"modified_minutes": 34682
},
"device": 2049,
"entropy": 7.94,
"extension": "",
"flags": {
"char_device": false,
"deleted": false,
"device": false,
"directory": false,
"hidden": false,
"immutable": true,
"link": false,
"named_pipe": false,
"regular": true,
"sgid": false,
"sgid_root": false,
"socket": false,
"sticky": false,
"suid": false,
"suid_root": false
},
"gid": 0,
"gid_name": "root",
"hash": {
"md5": "7275d8b380e6facc7c5420603f2672cc",
"sha1": "1a6ad6106aa4dacb6fc8262169779f743b9255bd",
"sha256": "98412571e95a5cdd24879389f846f3571d5975a92a4d467d292e4c1d6a481cef",
"sha512": "b664e43a878f7a598fd656b31a0eb687533bd9689e22803051cd32d64205518e7b16e715c16a476e471f25dc0368922c33cc519becdc7a7ac41916a494ab85eb"
},
"inode": 135430,
"magic_num": {
"class": "executable_linux",
"expected_extensions": [],
"hex": "7f454c46020101030000",
"text": "ELF\u0002\u0001\u0001\u0003\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0002\u0000>\u0000",
"type": "elf"
},
"mode": "0100755",
"name": "kthreadd",
"nlink": 1,
"path": "/usr/bin/kthreadd",
"path_link": "",
"path_root": "/usr/bin/",
"rdevice": 0,
"size": 1274136,
"size_byte_count": 1274136,
"size_mismatch": false,
"uid": 0,
"uid_name": "root"
},
"cgroup": [
{
"controller_list": "freezer",
"hierarchy_id": "11",
"path": "/"
},
{
"controller_list": "devices",
"hierarchy_id": "10",
"path": "/system.slice/systemd-journald.service"
},
{
"controller_list": "cpuset",
"hierarchy_id": "9",
"path": "/"
},
{
"controller_list": "blkio",
"hierarchy_id": "8",
"path": "/system.slice/systemd-journald.service"
},
{
"controller_list": "cpuacct,cpu",
"hierarchy_id": "7",
"path": "/system.slice/systemd-journald.service"
},
{
"controller_list": "perf_event",
"hierarchy_id": "6",
"path": "/"
},
{
"controller_list": "hugetlb",
"hierarchy_id": "5",
"path": "/"
},
{
"controller_list": "pids",
"hierarchy_id": "4",
"path": "/system.slice/systemd-journald.service"
},
{
"controller_list": "net_prio,net_cls",
"hierarchy_id": "3",
"path": "/"
},
{
"controller_list": "memory",
"hierarchy_id": "2",
"path": "/system.slice/systemd-journald.service"
},
{
"controller_list": "name=systemd",
"hierarchy_id": "1",
"path": "/system.slice/systemd-journald.service"
}
],
"cmdline": "/usr/bin/kthreadd",
"command": "kthreadd",
"container": {
"id": "",
"id_short": "",
"upperdir": "",
"workingdir": ""
},
"cwd": "/",
"date": {
"created": "2021-07-19T23:53:48+12:00",
"created_minutes": 545
},
"entropy": 7.94,
"environ": [
"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin",
"_=/usr/bin/kthreadd",
" =/usr/bin/bioset",
"PWD=/",
"LANG=en_NZ.UTF-8",
"NOTIFY_SOCKET=/run/systemd/notify",
"SHLVL=2",
"WATCHDOG_PID=471",
"WATCHDOG_USEC=180000000",
""
],
"extension": "",
"file_descriptors": [
{
"class": "device",
"number": 0,
"path": "/dev/null",
"type": "block"
},
{
"class": "device",
"number": 8,
"path": "pipe:[8506748]",
"type": "pipe"
},
{
"class": "unknown",
"number": 11,
"path": "anon_inode:[eventfd]",
"type": "unknown"
},
{
"class": "device",
"number": 12,
"path": "/dev/null",
"type": "block"
},
{
"class": "device",
"number": 4,
"path": "pipe:[8506749]",
"type": "pipe"
},
{
"class": "unknown",
"number": 3,
"path": "anon_inode:[eventpoll]",
"type": "unknown"
},
{
"class": "unknown",
"number": 5,
"path": "socket:[8506728]",
"type": "socket"
},
{
"class": "device",
"number": 6,
"path": "pipe:[8506749]",
"type": "pipe"
},
{
"class": "device",
"number": 1,
"path": "/dev/null",
"type": "block"
},
{
"class": "unknown",
"number": 10,
"path": "anon_inode:[eventfd]",
"type": "unknown"
},
{
"class": "tcp",
"number": 13,
"path": "socket:[9420771]",
"type": "socket"
},
{
"class": "device",
"number": 2,
"path": "/dev/null",
"type": "block"
},
{
"class": "device",
"number": 7,
"path": "pipe:[8506748]",
"type": "pipe"
},
{
"class": "unknown",
"number": 9,
"path": "anon_inode:[eventfd]",
"type": "unknown"
}
],
"flags": {
"containerized": false,
"deleted": false,
"hidden": false,
"immutable": true
},
"gid": 0,
"gid_name": "root",
"hash": {
"md5": "7275d8b380e6facc7c5420603f2672cc",
"sha1": "1a6ad6106aa4dacb6fc8262169779f743b9255bd",
"sha256": "98412571e95a5cdd24879389f846f3571d5975a92a4d467d292e4c1d6a481cef",
"sha512": "b664e43a878f7a598fd656b31a0eb687533bd9689e22803051cd32d64205518e7b16e715c16a476e471f25dc0368922c33cc519becdc7a7ac41916a494ab85eb"
},
"maps": [
"00400000-00401000 r--p 00000000 00:00 0 ",
"00401000-006f0000 r-xp 00000000 00:00 0 ",
"006f0000-007a2000 r--p 00000000 00:00 0 ",
"007a2000-00843000 rw-p 00000000 00:00 0 ",
"01147000-01190000 rw-p 00000000 00:00 0 [heap]",
"01190000-011b0000 rw-p 00000000 00:00 0 [heap]",
"7f6394000000-7f6394021000 rw-p 00000000 00:00 0 ",
"7f6394021000-7f6398000000 ---p 00000000 00:00 0 ",
"7f639c000000-7f639c021000 rw-p 00000000 00:00 0 ",
"7f639c021000-7f63a0000000 ---p 00000000 00:00 0 ",
"7f63a0000000-7f63a0021000 rw-p 00000000 00:00 0 ",
"7f63a0021000-7f63a4000000 ---p 00000000 00:00 0 ",
"7f63a4000000-7f63a4021000 rw-p 00000000 00:00 0 ",
"7f63a4021000-7f63a8000000 ---p 00000000 00:00 0 ",
"7f63a939c000-7f63a939d000 ---p 00000000 00:00 0 ",
"7f63a939d000-7f63a9b9d000 rw-p 00000000 00:00 0 ",
"7f63a9b9d000-7f63a9b9e000 ---p 00000000 00:00 0 ",
"7f63a9b9e000-7f63aa39e000 rw-p 00000000 00:00 0 ",
"7f63aa39e000-7f63aa39f000 ---p 00000000 00:00 0 ",
"7f63aa39f000-7f63aab9f000 rw-p 00000000 00:00 0 ",
"7f63aab9f000-7f63aaba0000 ---p 00000000 00:00 0 ",
"7f63aaba0000-7f63ab3a0000 rw-p 00000000 00:00 0 ",
"7f63ab3a0000-7f63ab3a1000 ---p 00000000 00:00 0 ",
"7f63ab3a1000-7f63abba1000 rw-p 00000000 00:00 0 ",
"7f63abba1000-7f63abba2000 r--p 00000000 08:01 135430 /usr/bin/kthreadd",
"7f63abcc5000-7f63abcd9000 r-xp 00000000 00:00 0 ",
"7ffdb36d9000-7ffdb36fa000 rw-p 00000000 00:00 0 [stack]",
"7ffdb37bd000-7ffdb37bf000 r-xp 00000000 00:00 0 [vdso]",
"ffffffffff600000-ffffffffff601000 r-xp 00000000 00:00 0 [vsyscall]"
],
"name": "kthreadd",
"network_ports": {
"established": true,
"established_num": 1,
"icmp": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"icmp6": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"listening": false,
"listening_num": 0,
"operating": true,
"raw": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"raw6": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"sctp": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"tcp": {
"connections": [
{
"ip_address_local": "REDACTED",
"ip_address_remote": "103.231.30.59",
"port_local": 42624,
"port_remote": 443
}
],
"established": true,
"established_num": 1,
"listening": false,
"listening_num": 0,
"operating": true
},
"tcp6": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"udp": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
},
"udp6": {
"connections": null,
"established": false,
"established_num": 0,
"listening": false,
"listening_num": 0,
"operating": false
}
},
"path": "/usr/bin/kthreadd",
"pgid": 6572,
"pid": 6572,
"ppid": 1,
"stack": [
"ep_poll+0x23e/0x360",
"SyS_epoll_wait+0xed/0x120",
"system_call_fastpath+0x25/0x2a",
"0xffffffffffffffff"
],
"state": "S",
"system_uptime": "2021-07-10T14:24:17+12:00",
"uid": 0,
"uid_name": "root"
},
"response": {
"directory": {
"error": false
},
"file": {
"error": false
},
"log": {
"error": false
},
"process": {
"error": false,
"killed": false,
"suspended": false
},
"user": {
"error": false
}
}
},
"severity": 3,
"start_time": "2021-07-19T20:59:10Z",
"status": "alert",
"status_msg": "ok",
"tags": [
"attack.id.T1027",
"attack.tactic.defense_evasion",
"attack.tactic.execution",
"process"
],
"type": "process",
"uid": 0,
"uid_username": "root"
}Malicious LD_PRELOAD Library
{
"end_time": "2021-07-19T20:57:13Z",
"engine": "sandfly_engine_file",
"euid": 0,
"euid_username": "root",
"exec_seconds": 4,
"name": "file_immutable_in_lib_dir",
"output_format": "3.0",
"pid": 54929,
"results": {
"explanation": "The file '/usr/lib/libcurl.so.2.17.0' is marked as immutable and was found under '/usr/lib/'. Immutable files are not common on Linux and often is done by malware to prevent itself from being deleted. Please investigate this file to be sure it is meant to be marked immutable and is not part of a malicious program or rootkit. It is owned by UID '0' and was created on 2021-06-26T06:59:10+12:00.",
"file": {
"blksize": 4096,
"blocks": 64,
"data": null,
"date": {
"accessed": "2021-07-19T20:26:50+12:00",
"accessed_minutes": 750,
"created": "2021-06-26T06:59:10+12:00",
"created_minutes": 34678,
"modified": "2021-06-26T06:55:12+12:00",
"modified_minutes": 34682
},
"device": 2049,
"entropy": 4.31,
"extension": ".0",
"flags": {
"char_device": false,
"deleted": false,
"device": false,
"directory": false,
"hidden": false,
"immutable": true,
"link": false,
"named_pipe": false,
"regular": true,
"sgid": false,
"sgid_root": false,
"socket": false,
"sticky": false,
"suid": false,
"suid_root": false
},
"gid": 0,
"gid_name": "root",
"hash": {
"md5": "fed81f7ec31811ac0d4fda157939504f",
"sha1": "c8a4039a4c347e9571ac042c43028f3d7e2b9784",
"sha256": "139adce4299a9c657347910061e0966482125c39b240eae5ee8b5b18de22c208",
"sha512": "1828a57ec9d6f83d99d23f93769ad74cb22323138b73a3cd7f784005da628b974152d4aa26bd25bf34aec3a5eedeb6a05cfc3138919aef252b92c5cafdf5da44"
},
"inode": 135428,
"magic_num": {
"class": "executable_linux",
"expected_extensions": [],
"hex": "7f454c46020101000000",
"text": "ELF\u0002\u0001\u0001\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0003\u0000>\u0000",
"type": "elf"
},
"mode": "0100755",
"name": "libcurl.so.2.17.0",
"nlink": 1,
"path": "/usr/lib/libcurl.so.2.17.0",
"path_link": "",
"path_root": "/usr/lib/",
"rdevice": 0,
"size": 31336,
"size_byte_count": 31336,
"size_mismatch": false,
"uid": 0,
"uid_name": "root"
},
"response": {
"directory": {
"error": false
},
"file": {
"error": false
},
"log": {
"error": false
},
"process": {
"error": false,
"killed": false,
"suspended": false
},
"user": {
"error": false
}
}
},
"severity": 3,
"start_time": "2021-07-19T20:57:09Z",
"status": "alert",
"status_msg": "ok",
"tags": [
"attack.tactic.persistence",
"file"
],
"type": "file",
"uid": 0,
"uid_username": "root"
}Malicious root SSH Key
The SSH key below was inserted by the malware into the root user's authorized_keys file to allow remote access.
{
"end_time": "2021-07-19T20:59:11Z",
"engine": "sandfly_engine_user",
"euid": 0,
"euid_username": "root",
"exec_seconds": 0,
"name": "user_ssh_authorized_keys_immutable",
"output_format": "3.0",
"pid": 54929,
"results": {
"explanation": "The SSH authorized_keys file for user 'root' is marked as immutable and was found under '/root/.ssh/authorized_keys'. Immutable SSH authorized_keys files are not common on Linux and often is done by malware to prevent credentials from being deleted. Please investigate this file to be sure it is meant to be marked immutable and is not part of a malicious program or rootkit. It is owned by UID '0' and was created on 2021-06-26T06:59:10+12:00.",
"response": {
"directory": {
"error": false
},
"file": {
"error": false
},
"log": {
"error": false
},
"process": {
"error": false,
"killed": false,
"suspended": false
},
"user": {
"error": false
}
},
"user": {
"gecos": "root",
"gid": 0,
"gid_name": "root",
"group_membership": null,
"home_dir": "/root",
"password": {
"age_max": 99999,
"age_min": 0,
"days_since_expired": 0,
"days_since_last_changed": 5,
"disabled": false,
"empty": false,
"hash": {
"md5": "bf1d75ea36725c891826d9863ed2b5ba",
"sha1": "97c44aaa7db98765b8ba9e5375fed7acc46dcd56",
"sha256": "27dae2857e4b6c627377cc996c2d2b906d1d29a411f3a03f537916419d933eb5",
"sha512": "e99e980a9058bf37921c00b63c325a8fd3e1b9d8a49acdc66bbcac9df7b61fe6351b77dc56a7c3dffeb638b3e7d5a5fa98926ec6dc7fed0b166ae306afc654e2"
},
"inactivity_period": 0,
"locked": false,
"present": true,
"reserved": "",
"type": "sha-512",
"warning_period": 7
},
"shell": "/bin/bash",
"ssh": {
"authorized_keys": {
"data": [
{
"comment": "rsa 2048-040119",
"entry": "ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAv54nAGwGwm626zrsUeI0bnVYgjgS/ux7V5phklbZYFHEm+3Aa0gfu5EQyQdnhTpo1adaKxWJ97mrM5a2VAfTN+n6KUwNYRZpaDKiUwmHNUSW7E1S18ClTCBtRsC0rRDTnIrslTRSHlM3cNN+MskKTW/vWz/oE3ll4MMQqexZlsLvMpVVlGq6t3XjFXz0ABBI8GJ0RaBS81FS2R1DNSCb+zORNb6SP6g9hHk1i9V5PjWNqNGXyzWIrCxLc88dGaTttUYEoxCl4z9YOiTw8F5S4svbcqTTVIu/zt/7OIQixDREGbddAaXZXidu+ijFeeOul/lJXEXQK8eR1DX1k2VL+w== rsa 2048-040119",
"entry_num": 1,
"hash": {
"md5": "e2d6943f010de84d3c2f108f6e245332",
"sha1": "559c2b1fa95ff99ce619a4c8f09a6ba1c8a38287",
"sha256": "62b8b5844975d78d59d3fb1b706f6507f6b2c0523e92655b931af2e756a97f59",
"sha512": "8d94c2ede768628017eaf08ecc248599a783f3e39d18c07376318f328ddf00dd3b506d4554c9a660e91685b97e04db3ac6aba3d2c642a5ac11054b0c6e6b81e8"
},
"key": "AAAAB3NzaC1yc2EAAAABIwAAAQEAv54nAGwGwm626zrsUeI0bnVYgjgS/ux7V5phklbZYFHEm+3Aa0gfu5EQyQdnhTpo1adaKxWJ97mrM5a2VAfTN+n6KUwNYRZpaDKiUwmHNUSW7E1S18ClTCBtRsC0rRDTnIrslTRSHlM3cNN+MskKTW/vWz/oE3ll4MMQqexZlsLvMpVVlGq6t3XjFXz0ABBI8GJ0RaBS81FS2R1DNSCb+zORNb6SP6g9hHk1i9V5PjWNqNGXyzWIrCxLc88dGaTttUYEoxCl4z9YOiTw8F5S4svbcqTTVIu/zt/7OIQixDREGbddAaXZXidu+ijFeeOul/lJXEXQK8eR1DX1k2VL+w==",
"options": "",
"path": "/root/.ssh/authorized_keys",
"type": "ssh-rsa"
}
],
"duplicate_found": false,
"file": [
{
"blksize": 4096,
"blocks": 8,
"data": null,
"date": {
"accessed": "2021-07-19T20:26:50+12:00",
"accessed_minutes": 752,
"created": "2021-06-26T06:59:10+12:00",
"created_minutes": 34680,
"modified": "2021-06-26T06:59:10+12:00",
"modified_minutes": 34680
},
"device": 2049,
"entropy": 5.93,
"extension": "",
"flags": {
"char_device": false,
"deleted": false,
"device": false,
"directory": false,
"hidden": false,
"immutable": true,
"link": false,
"named_pipe": false,
"regular": true,
"sgid": false,
"sgid_root": false,
"socket": false,
"sticky": false,
"suid": false,
"suid_root": false
},
"gid": 0,
"gid_name": "root",
"hash": {
"md5": "a4bcd006b681d3ef99c3c28be376116e",
"sha1": "1c59c1c28754d015a79d98b4868a700ba2184af3",
"sha256": "ccadae0c6dc8985186f4d639f5ba7dd262cd95253158e468613a4e53d1f1578a",
"sha512": "8d427a01ae69ec00324b08a465dda067426c6a4bbc040bedb2ede695b214752821ba7296171815f141712f93ba7a6cdd037c2a3b855da55a1bd637b51be29b1e"
},
"inode": 396458,
"magic_num": {
"class": "unknown",
"expected_extensions": null,
"hex": "7373682d727361204141",
"text": "ssh-rsa AAAAB3NzaC1y",
"type": "unknown"
},
"mode": "0100644",
"name": "authorized_keys",
"nlink": 1,
"path": "/root/.ssh/authorized_keys",
"path_link": "",
"path_root": "/root/.ssh/",
"rdevice": 0,
"size": 396,
"size_byte_count": 396,
"size_mismatch": false,
"uid": 0,
"uid_name": "root"
}
],
"present": true,
"total": 1
}
},
"uid": 0,
"username": "root"
}
},
"severity": 3,
"start_time": "2021-07-19T20:59:11Z",
"status": "alert",
"status_msg": "ok",
"tags": [
"attack.id.T1021.004",
"attack.id.T1078",
"attack.id.T1098.004",
"attack.tactic.initial_access",
"attack.tactic.lateral_movement",
"attack.tactic.persistence",
"user"
],
"type": "user",
"uid": 0,
"uid_username": "root"
}Full Key:
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAv54nAGwGwm626zrsUeI0bnVYgjgS/ux7V5phklbZYFHEm+3Aa
0gfu5EQyQdnhTpo1adaKxWJ97mrM5a2VAfTN+n6KUwNYRZpaDKiUwmHNUSW7E1S18ClTCBtRsC0rRDTnIrslT
RSHlM3cNN+MskKTW/vWz/oE3ll4MMQqexZlsLvMpVVlGq6t3XjFXz0ABBI8GJ0RaBS81FS2R1DNSCb+zORNb6
SP6g9hHk1i9V5PjWNqNGXyzWIrCxLc88dGaTttUYEoxCl4z9YOiTw8F5S4svbcqTTVIu/zt/7OIQixDREGbdd
AaXZXidu+ijFeeOul/lJXEXQK8eR1DX1k2VL+w== rsa 2048-040119