Linux Security,
it's all we do.
Sandfly's deep understanding of Linux intruder tactics offers unparalleled threat coverage and proactive protection. Known and unknown attacks are detected with safety and performance.
Linux threats unmasked.
Ride along with Sandfly as we hunt for compromised Linux systems on our firing range.
Watch the VideoUse Cases
One tool for all monitoring
Sandfly's compatibility means one tool can watch all your Linux assets. Our built-in threat detection modules, and our active defense features like SSH key tracking, gives Sandfly extensive coverage.
Embedded devices and appliances
Sandfly can run on notoriously difficult to monitor embedded devices and Linux-based appliances. Everything from the cloud to the edge can be secured.
Air-gapped and sensitive networks
Sandfly does not send any data offsite for analysis by us or any other third-party. This means we work on isolated and air-gapped networks and sensitive telemetry data never leaves your control.
Works with other EDR solutions
Sandfly's active threat hunting works with agent-based EDR systems and provides visibility where agents cannot go. Sandfly provides a unique and powerful second set of eyes to traditional EDR.
Distribution agnostic
Sandfly is Linux distribution agnostic. If the system to be monitored runs Linux, chances are very high Sandfly can protect it with little risk.
Critical infrastructure
Sandfly is trusted by critical infrastructure providers globally to protect their systems. We have a proven track-record of performance, stability, and safety in this role.
Build your own threat hunting modules
Customize your Linux security with Sandfly's easy-to-use checks and hunt down threats specific to your needs. Access over 1,100 pre-built detections and create your own with our intuitive syntax. Get instant insights on attackers and leverage our expertise in Linux forensics. Explore just some of the Linux threats we combat below.
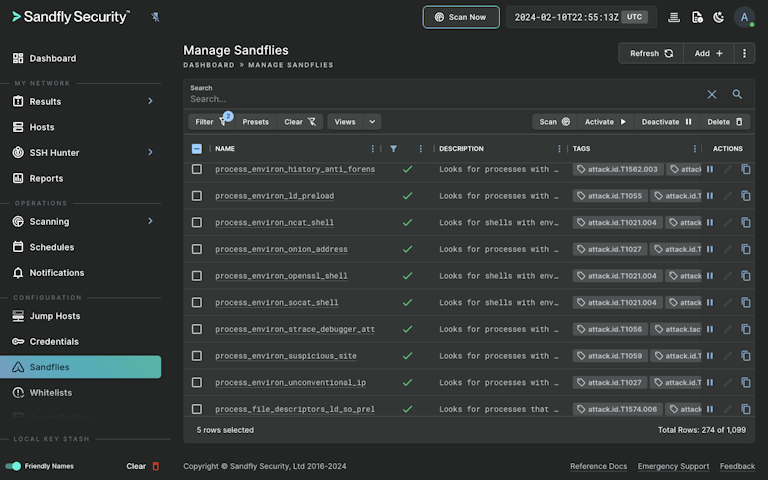
Sandfly finds these and many more Linux attack tactics
Loadable Kernel Module and eBPF stealth rootkit detection
Standard rootkit detection
Cryptocurrency and cryptominer detection
Weak and default Linux user passwords
Hidden and suspicious processes
Processes performing suspicious network activity
Process masquerading
File masquerading and hiding
Poisoned system commands
Cloaked data from stealth rootkits
Tampered system start-up scripts
Encrypted and suspicious executable files
Unusual system binaries
Suspicious users and permissions
Hidden executables
System shells being used or concealed in suspicious ways
Process injection
Reverse bindshell exploits
Standard bindshell exploits
Compromised websites
Tampered audit records
Destroyed audit records
Webshells and backdoors
Anti-forensics activity
Cloaked backdoors
Privilege escalation backdoors
Malware persistence mechanisms
SSH keys being misused or orphaned
Suspicious user login and logout activities
Suspicious cron jobs and other scheduled tasks
Linux malware and Advanced Persistent Threat activity
Distributed Denial of Service (DDoS) agents
Password and network sniffers
Many others!