Track SSH keys,
and who uses them
SSH keys pose serious risks to Linux, including unauthorized access and stealthy lateral movement. Sandfly tracks critical SSH assets agentlessly. We call this capability SSH Hunter.
With SSH Hunter, all SSH public keys are tracked and traced. Security teams can see where keys are being used, who is using them, when they first appeared, and what they allow access to across all systems instantly.
SSH key hunting.
Ride along with Sandfly as we hunt for compromised SSH keys on our firing range.
Watch the VideoUse Cases
Know where SSH keys are
A stolen SSH key can allow instant access to your entire infrastructure. Sandfly ensures SSH keys only allow access where they should and new keys do not show up unexpectedly.
Safeguard embedded devices
SSH keys can allow silent access to embedded devices. Know who and what has access to these systems with Sandfly.
Monitor Linux appliances
Linux appliances often present a black box to security teams. Sandfly can gain access to these systems and let you see what SSH access is being allowed instantly.
Key and server risks
Sandfly can identify SSH key risks such as duplicate keys or weak keys using older algorithms. We also have policy checks to detect vulnerable settings on your SSH servers.
Key timeline
Our SSH timeline provides a window into key movement and activity. Sandfly shows you when keys were first seen, last seen, or even if they vanished and returned at a later date.
Try SSH hunter
Don't let hidden threats compromise your network security. Start your free trial today.
Get A Trial LicenseAutomatically track and audit SSH credentials
SSH Hunter leverages Sandfly's agentless architecture to give you the following benefits.
Combat unauthorized access
Sandfly proactively identifies SSH risks, mitigating threats such as credential compromise and unauthorized access. Tracking SSH keys prevents data breaches and improves your organization's cybersecurity posture.
Configuration error detection
Automates SSH credential monitoring reducing the likelihood of errors that can expose your organization to compromise. Sandfly ensures your SSH credentials are constantly monitored and tracked.
Unparalleled performance
Our platform integrates seamlessly with your existing infrastructure, providing protection without impacting system performance. SSH key tracking is immediate, automatic, and fast.
Compliance and asset tracking
Sandfly simplifies compliance and asset tracking by offering deep visibility into your SSH environment, ensuring you maintain an audit-ready posture.
Scalable solution
As your enterprise expands, our agentless solution scales with you ensuring your SSH environments remain secure. Risks of SSH credential compromise are consistently monitored and managed.
Try SSH Hunter
Don't let hidden threats compromise your network security. Start your free trial today and experience the power of proactive SSH security.
Get A Free LicenseTrack SSH key use and abuse
Being agentless, Sandfly will automatically find and track SSH keys without any user intervention or risk to remote systems. Once we identify keys, they are tracked and customers can use a variety of tools to stay on top of SSH credential use and abuse.
The SSH Key Explorer allows you to visually see where a key is being used across your Linux fleet, who is using the key, when it was created, how old it is, and much more. You get an instant view of what SSH keys are in use across your network.
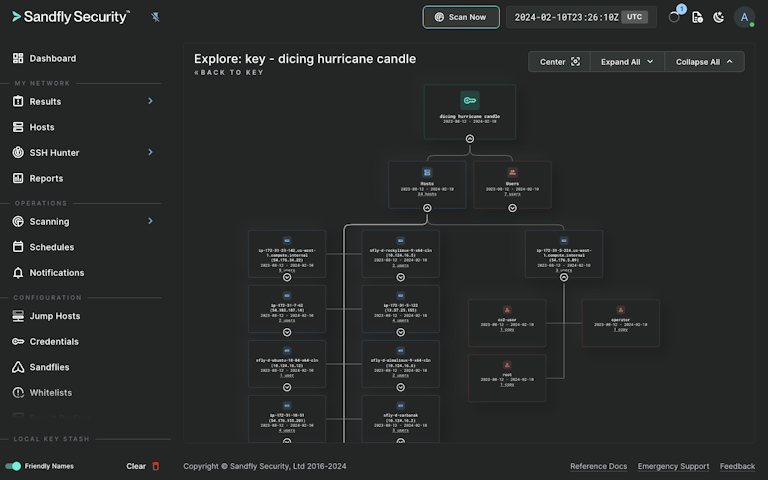
Rapid incident response
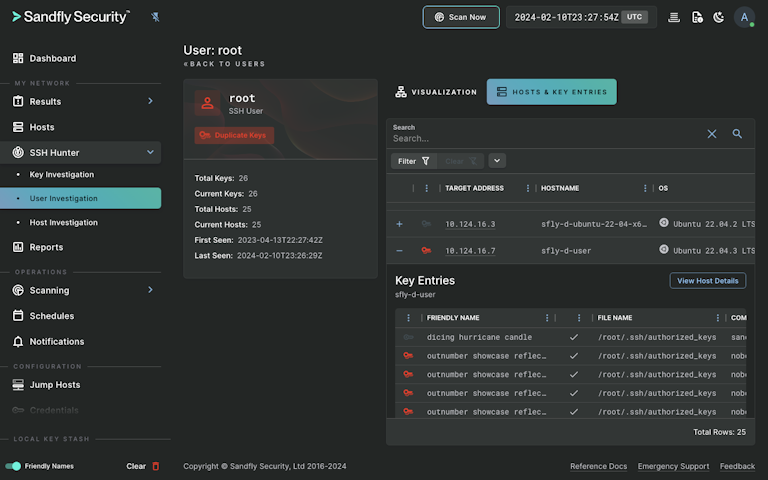
If you are responding to an incident, knowing what SSH credentials are in use is critical. SSH keys are high value targets for intruders and allow rapid compromise across an enterprise. With Sandfly's agentless scanning for SSH keys, you get instant knowledge of this critical piece of forensic data even if no monitoring is currently in place. Sandfly will automatically locate SSH keys on hosts and build an instant overview of what is happening with them to save precious time when investigating an incident.
SSH key auditing made easy
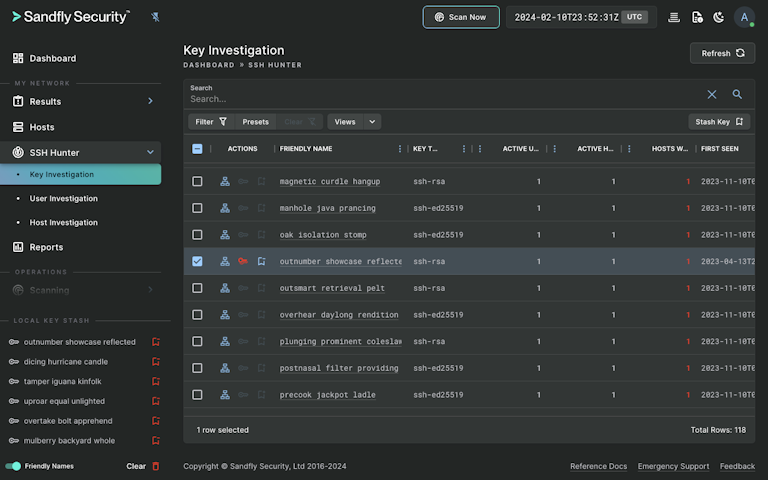
SSH Hunter also tracks keys and looks for unusual behaviors such as duplicate keys, orphaned keys, and more. Our key timeline shows you the first time we saw a key, and when that key was seen on other hosts. You will know at a glance if a new key is being used unexpectedly or if old keys are still present on any host.
SSH credential compromise presents significant risks that demand a proactive, performance-conscious solution. Sandfly Security offers an agentless approach to protect your SSH environments, track assets, and ensure comprehensive security without compromising system performance.
Audit your SSH keys today
Experience the benefits of proactive threat detection, seamless integration, and SSH asset tracking.
Protect Hosts Now